The Verizon Data Breach report was published this week, with a handful of insight gathered from the most comprehensive set of data about last year's breaches. While it is highly recommended to read the report in full, we believe there are a few key takeaways:
1. Security still lags with detection
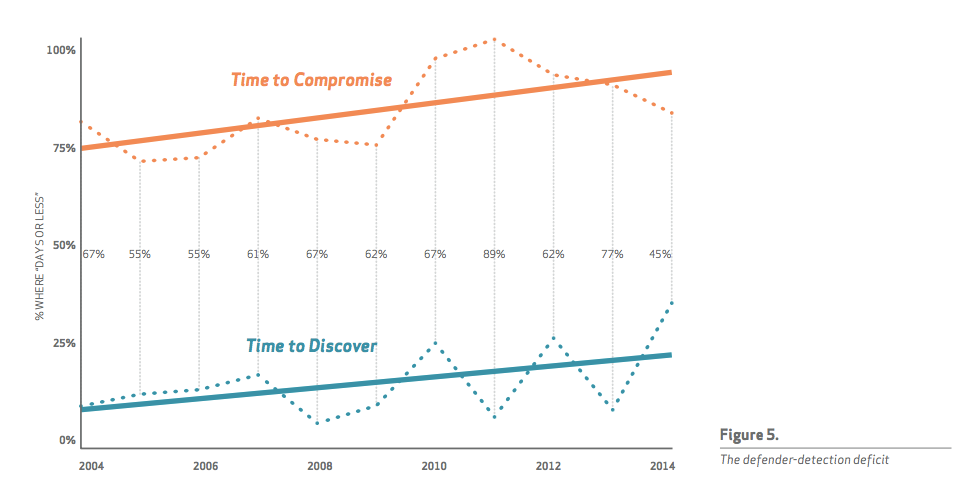
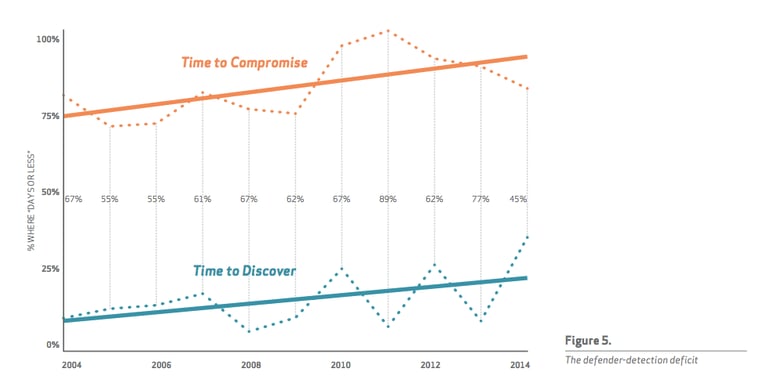
I love the way DBIR visually presents the data. The figure below clearly shows how in most of the attacks, the compromise happens within a few days or less. In fact, according to DBIR, in 60% of cases the compromise happens within minutes or less.
The graph shows how often attackers are able to compromise a victim in days or less (orange line) with how often defenders detect compromises within that same time frame (teal line). The sad news - even though there was a slight improvement in 2014, detection is still slow. Too slow.
At Cybereason, we believe its time to shift this paradigm. Detection should become immediate.
2. Sharing is cyber-caring”, but context is key
We loved DBIR's analysis on threat intelligence "Sharing is Caring". It is great to see how threat sharing has evolved over the years and we greatly support any initiative that spreads knowledge about attack vectors. But information sharing is only one side of the security intelligence coin. The other side is the ability to analyze, comprehend and make that information relevant to the individual organization. Or in the DBIR’s words: "Certainly, anything that leads to the discovery of an incident is worthwhile, but in most cases, context is key. Those consuming threat intelligence, let it be known: Focus less on being led to water and work on characterizing where the well resides. Expect more out of your communities, and where possible, reciprocating context enables a wider audience to make additional determinations that enable a broader defensive capability.
At Cybereason, we believe context is essential for detection and response. Being able to connect between external intelligence and internal behaviours, to cross-reference them and build a picture of the malicious activity is our approach for handling the “what do I do with this info” trend caused by the ubiquity of security threat feeds.
3. Special snowflakes fall on every backyard”
The DBIR clearly confirms that malware nowadays are unique. 70–90% of malware samples are unique to an organization. This means that signature-focused detection is dead, as it could not detect the various modifications to the code or the hashes frequently introduced to the malware.
At Cybereason, our approach is to look at Malops - a complete malicious operation. That includes not only a detection of malware, but also the related malicious behaviors and communication. By doing so, we take a more holistic approach to detection, enabling detection of unknown malware as well as non-malware based operations.