Various high-profile attacks have shown how a simple, vulnerable public Web server can seriously damage an organization’s reputation by harming the application’s users and, in some cases, can initiate an attack on the organization’s internal network. Traditional security tools remain ineffective in this detecting this threat. EDR solutions, though, provide a new approach to solving this detection problem.
So why are attackers interested in compromising Web servers?
The standard architecture of public Web servers can prove advantageous for attackers. By their nature, public Web servers handle requests from the Internet and typically have two network interfaces:
- External to DMZ (web server) - Receive requests from unknown Web/users.
- DMZ (web server) to Internal - Deliver data to internal resources and manage the web server by internal users.
Attackers focus their efforts on compromising Web servers because they offer the ability to run the entire attack campaign remotely and usually store sensitive information. Infiltrating these middle layer servers can be the easiest way to penetrate an organization’s internal network.
After compromising the servers, attackers can query and move deeper into the internal network using legitimate network channels and connected resources such as databases, user management interfaces and other Web applications.
Here’s how a compromised public Web server fits with the attack lifecycle:
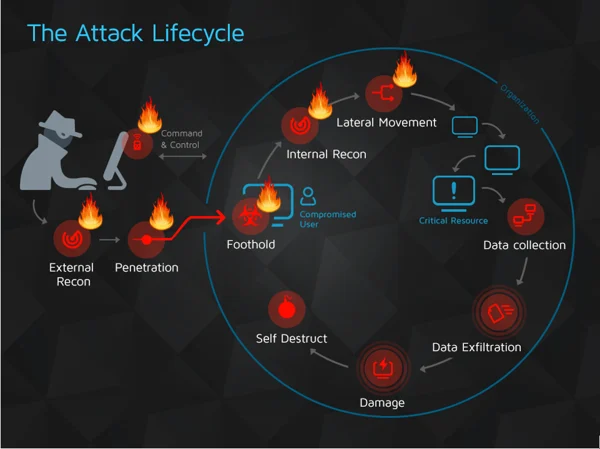
External reconnaissance – Map and scan all publicly exposed Web servers remotely.
Penetration – Abuse the Web servers to penetrate the organization network.
Command and control – Control the remote Web server from the Internet using HTTP requests or a newly crafted channel.
Foothold – Get full control over the remote Web server by obtaining the credentials of the highest privileged user and establishing persistence. In many cases, the Web server will be targeted in the last stage of the attack to create, for example, a backdoor for easy return.
Internal reconnaissance – Use the compromised Web server to gain information regarding the internal network and its sensitive assets.
Lateral movement – Pivot inside the internal network and continue the attack from other internal endpoints or servers.
All of these stages can be carried out remotely.
The attack surface is extremely wide and many different techniques can be used to ultimately reach the same result: a compromised Web server that can later be used to to a compromised network. Some of the techniques that can be used to compromise a Web server include:
- Web application attacks, such as injection techniques like RFI/LFI, XXE
- Web shells
- Known (and to be known) exploits and zero days in specific frameworks such as ShellShock (a CGI-based web server vulnerability), Apache Struts, JAVA Spring (a blog post published by Tushar Adhikary explains this in detail).
- Exposed admin interfaces with configuration weaknesses that could allow the uploading of malicious files to the Web server and, in some cases, even allow direct interaction with server's OS.
To solve this problem, an entire security subdomain has emerged, filled with solutions that aim to prevent Web applications from being exploited. And for good reason: Web-based attacks cost companies $2 million in 2017, according to Accenture. The damage Web application attacks can cause isn’t new to the security community, which has researched this attack vector since the dawn of the Web.
Among the many security solutions that attempt to deal with Web application attacks include Web application firewalls, vulnerability scanners, static code analysis and Web isolation. Some solutions try to prevent attacks and others help after a breach is discovered. Unfortunately, none of them is generic enough to cover all the attacker’s options. These solutions are mainly based on signatures and string matching, and are not likely to be effective against unknown and uncommon attack vectors. And they can’t detect sophisticated and targeted attacks carried out by skilled adversaries whose ability to compromise an organization constantly improves with the discovery of zero-days and new attack methods. In other words, the solutions that exist are ineffective.
USING BEHAVIORAL ANALYSIS TO DETECT COMPROMISED WEB SERVERS
This rapidly evolving threat landscape increases the challenge of detecting sophisticated attacks.
Web shells are a great example of a Web attack technique that can be difficult to detect. Known Web shells can be easily modified or obfuscated, making circumventing solutions like antivirus, YARA rules and other tools that use known indicators easy.
Here’s an example that shows how slightly tweaked Web shells can be used in attacks. Cisco’s incident response team, Talos, published a detailed technical post about Nyetya, a massive ransomware attack on organizations in the Ukraine in 2017. The attackers compromised a Web server using “a slightly modified version of the open source PHP webshell PAS” as a backdoor to execute their malicious activities, according to Talos.
And Web server vulnerabilities are always being discovered. For instance, in 2017 vulnerabilities discovered in Apache Struts allowed attackers to execute code remotely on Web servers. Apache released a patch, but patching production servers is a complex and costly process for many organizations. Examining the Equifax breach shows how patch update procedures are not always easy to deploy.
Cybereason’s EDR platform detects compromised Web servers, regardless of the vector or tool used, by relying on behavioral analysis and machine learning. Cybereason collects data from multiple endpoints and servers in real time and uses an in-memory graph to cross correlate this data to discover malicious activity. Instead of using signatures that can be easily changed, Cybereason looks for attack behavior.






