TechCruch recent article claims that detection is a "must have" in today's complex breach environment, and can replace the old prevention/protection paradigm of security.
Organizations must assume they will be compromised, no matter how great their protection systems are. This is due to the fact that today's cyber attacks are well planned, well crafted and well targeted. It is not only the very vulnerable and unprotected organizations that are breached; it is also the best secured, most equipped companies, even those that employ the best security talents. This is evidenced in the recent JP Morgan Chase breach
But we have good news! The breach by itself, e.g. penetration into an organization's network, happens after the attackers spend weeks collecting intel inside the network. This helps them move laterally within a network and brings them closer to reaching their true goal and to create an actual damage. Stopping the attackers while they are inside the network, prior to them reaching their goal is a better, more possible approach than hoping to prevent penetration.
We believe TechCrunch's visual did a great job of explaining the time frame that detection has to act:
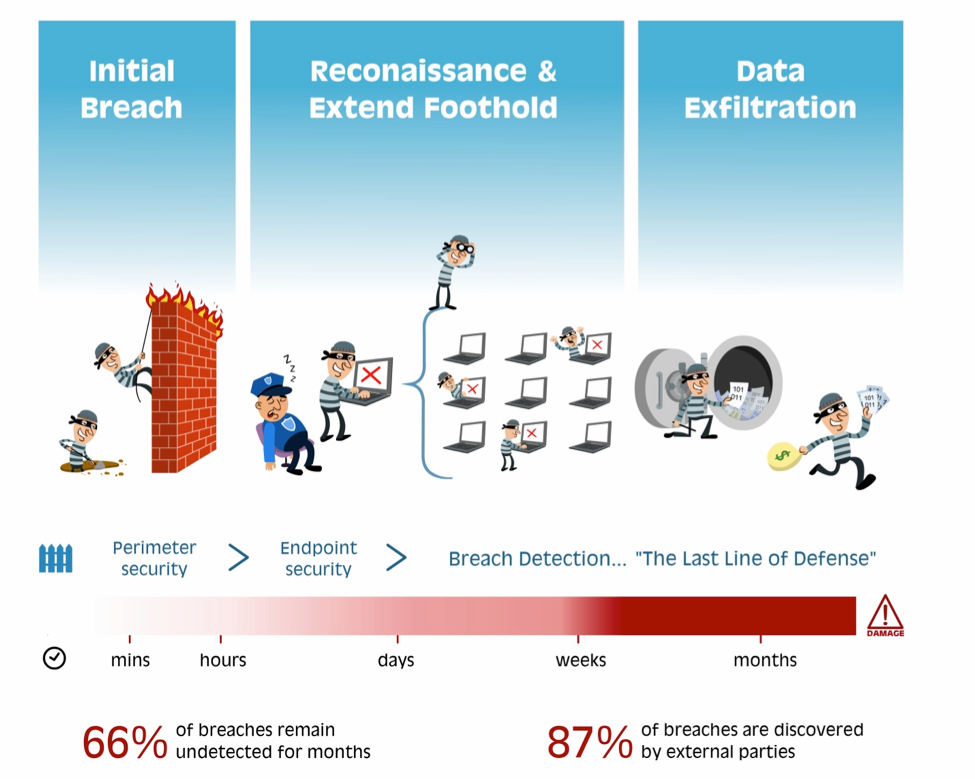
While not easy to deliver, real time detection is the new security paradigm that must be deployed in the era of complex hacking operations.





