
Ransomware: Which Industries Are Most Likely to Pay
Paying a ransom is the worst possible strategy for addressing ransomware attacks.

Yossi Rachman
May 12th 2020 marked the 3 year anniversary of the WannaCry ransomware attack. Estimated to have affected hundreds of thousands of endpoints across 150 countries all around the world, the total damages as a result of the WannaCry attack have reached up to 4 billion USD, according to some accounts.
The WannaCry ransomware itself used two separate NSA-developed exploits to infect endpoints and propagate across entire networks. Using the DoublePulsar backdoor tool developed by the NSA and leaked online by the Shadow Brokers attack group, the WannaCry ransomware installed and executed a copy of itself on a compromised endpoint. It then encrypted the endpoint’s data and infected other endpoints using the EternalBlue exploit (another NSA tool leaked by the Shadow Brokers) which abused a vulnerability in the implementation of the SMB v1 protocol in unpatched Microsoft Windows operating systems, and finally presented a ransom message demanding bitcoin payment in order to release the encrypted data.
The WannaCry attack, along with a number of additional ransomware attacks that either resurfaced or were especially repurposed with newly leaked NSA exploits, make up a period known by some cybersecurity practitioners as the 2017 Summer of Hell (not to be confused with New York commuters’ 2017 Summer of Hell).
This cybersecurity Summer of Hell, with its wave after wave of ransomware attacks, demonstrated the devastating damage-potential of cyberattacks in general and ransomware in particular. When considering that the ransomware attacks also crippled the UK’s National Health Services and caused life-saving surgeries and other treatments to be postponed or even cancelled, thereby resulting in loss of human life, the damage potential becomes appalling.
The 2017 Summer of Hell is considered by many to be the biggest wave of ransomware outbreaks in the brief history since this specific type of malware was introduced. However the havoc caused by the 2017 ransomware attacks was just the latest in a very dubious chain of evolution. In the 3 years that have passed since, attackers have been constantly upgrading and modernizing these weapons of mass disruption, in order to both maximize their own monetary gains and cause more widespread disruption.
One such example is the rise in Ransomware-as-a-Service (RaaS) or Ransomware Affiliate programs. Out of the numerous cases and variants from the last couple of years, in which the actual attacker (i.e. affiliate) does not need to have any type of deep technical skills other than the ability to disseminate phishing emails or trick people into double-clicking a file, there is one particular example that deserves special note.
The GandCrab ransomware first emerged in early 2018, and offered its participants, or as the people behind GandCrab addressed them - “traffic sellers, spammers, and people who have a regular source of installs” - a 60/40 profit share of victims’ ransom payments. On top of similar RaaS services offerings, GandCrab’s creators promised focus on performance, flexibility and reliability, while providing continuous support and updates of their product as well as technical support for participants.
Within about a year after it began to circulate, during which GandCrab was constantly updated and maintained with great effort invested in making its evasion mechanisms more and more advanced to minimize chances of its detection and prevention by different security solutions, the creators of GandCrab announced the affiliate program’s termination. In their notice, they claimed to have earned themselves more than “US $150 million in one year” and that they are “living proof that you can do evil and get off scot-free”. With this, the official GandCrab affiliate program ceased operations after claiming to have earned over US $2 billion for its various participants, with hundreds of thousands of victims - organizations and private individuals - and, based on some estimates, owning almost half of the global RaaS market.
Nevertheless, even after the termination of GandCrab’s official program, RaaS and modern variants of GandCrab itself are still operating today.

The GandCrab Ransomware affiliate program ad.
Another example is the recently added “value” of doxxing or publishing sensitive data leaked from compromised organizations in case the ransomware victim fails to pay the ransom. Unlike the ransomware of yore, these variants leak data out of the compromised endpoint to an attacker-controlled server before encrypting any of it. The leaked data is then used as another incentive - sometimes even a more expensive one - in order to ensure the victim pays up.
This technique is aimed at tackling many cases in which organizations are able to recuperate from a seemingly-devastating attack thanks to readily-available backups and well-structured business continuity plans.
The threat of publishing the leaked data taps into the fear and potential reputational, business and regulatory damages from having private data, sensitive intellectual property, financial information, and even user credentials, published online for all the world to see.
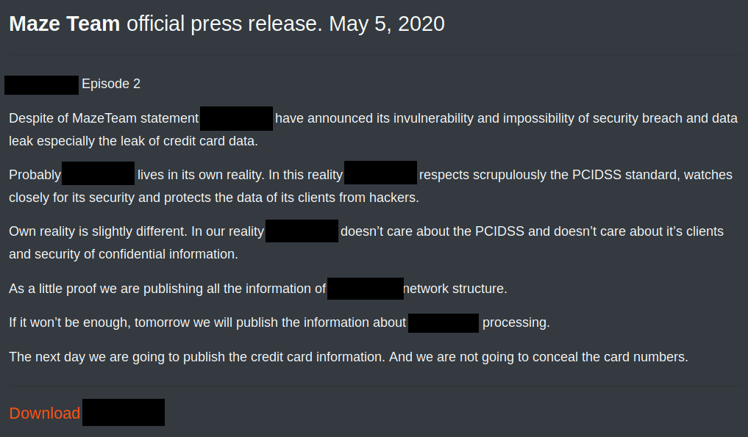
Example of one the posts on the Maze malware public “shaming website”.
A third example of emerging ransomware threats focuses on Operational Technologies (OT) networks and devices and industrial control systems (ICS). This last family of ransomware have been targeting industrial and medical businesses all over the world, and we have seen a special rise in cases since the beginning of the COVID-19 pandemic.
Aiming to hit systems that are left unpatched either due to legacy software controlling the industrial systems that would simply not run on modern operating systems, or that are too sensitive to withstand most patch and restart cycles, these threats are seldom faced with any security mechanisms.
In many cases, systems being hit are paradoxically excluded from business continuity plans due to their high sensitivity. As a result, any downtime they suffer, not to mention complete lockout due to ransomware attack, is absolutely catastrophic for most organizations, resulting in an almost immediate willingness to pay the ransom.
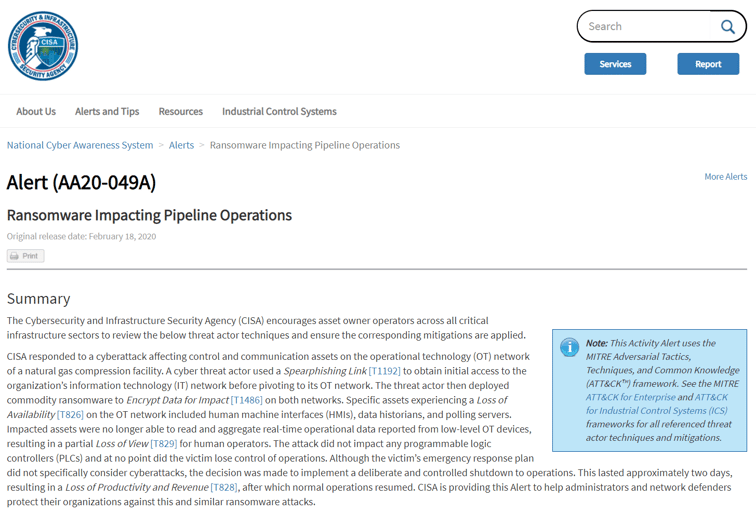
US-CERT alert AA20-049A on Ransomware Impacting Pipeline Operations
Unlike some estimates, it seems that ransomware is here to stay. Whenever there’s a decline in ransomware cases, or other more popular threats seem to be on the rise, new innovative techniques and even offerings seem to emerge. The reason for this is very simple - where there’s a demand for easy and discreet money, there will be supply.
That said, ransomware attacks can be mitigated, and the potential damage can be minimized through tried and tested methods:
Check out our latest whitepaper, Ransomware Decoded, for a glimpse of what modern ransomware looks like and how they're evading legacy prevention solutions.

Yossi Rachman is Director of Security Research at Cybereason.
All Posts by Yossi Rachman
Paying a ransom is the worst possible strategy for addressing ransomware attacks.

Cybereason has been tracking the Conti ransomware gang since 2020 and they have conducted hundreds of attacks against hospitals, law enforcement agencies and critical infrastructure operators...

Paying a ransom is the worst possible strategy for addressing ransomware attacks.

Cybereason has been tracking the Conti ransomware gang since 2020 and they have conducted hundreds of attacks against hospitals, law enforcement agencies and critical infrastructure operators...
Get the latest research, expert insights, and security industry news.
Subscribe