Malicious code can be detected by either looking at what it is or at what it does. The first method is the simpler and older of the two and uses the code’s static properties like its binary hash, contained binary sequences and strings, name, entropy or imported functions.
However, ransomware-on-demand services and self-modifying code easily generate completely new code with the same functionality, making this detection method obsolete. The ransomware distribution system described by Cybereason in its Operation Kofer research is just one example of an attack where each victim was infected with a unique ransomware binary. In addition, ransomware is the preferred payload for drive-by download and malvertising campaigns. Both of these attacks infect victims without their knowledge, and unfortunately, spam filters and sandbox email scanning systems cannot prevent them.
This means the only realistic way to detect ransomware is by looking at what it does. In other words, the heuristic behavioral approach. But there’s a catch - ransomware has several key differences that make it stand out from other malicious programs.
Ransomware isn’t subtle
Most malware silently persists in the network, carefully surveying the network surroundings, awaiting instructions or the right opportunity to attack. These programs mask their actions to evade detection and attempt to gain elevated privileges. Ransomware, on the other hand, wants to be discovered. As soon as the program starts encrypting files, it reveals itself to the victim and demands a hefty ransom, many times along with various threats.
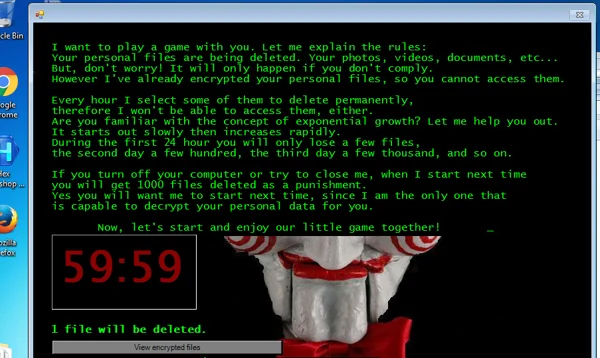
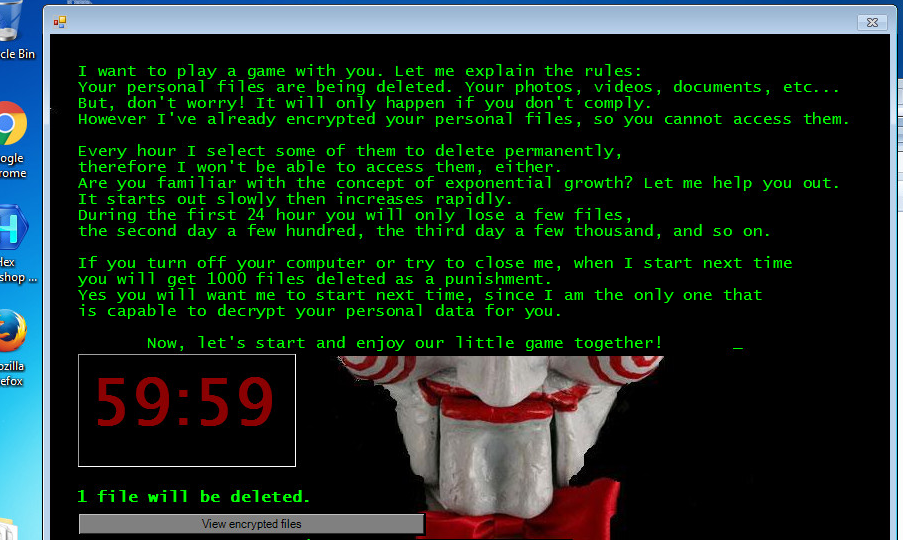
The Jigsaw ransomware letting us know it’s here
Cybereason’s research into ransomware strains show that while there are some very sophisticated, many are crude and poorly written. But just like an improvised weapon, the less refined strains are easy to produce and can be extremely effective. A piece of malicious code that promotes its existence upends the way most traditional anti-malware products work. You may think that lacking intricate malicious mechanisms makes ransomware easier to detect. But often times malicious behaviors and techniques are malware’s weak spots and make these programs stand out to defenders.
Ransomware doesn’t need to be accurate
Banking Trojans steal credit card numbers and bank account details by carefully extracting them from specific locations in the browser when it accesses specific domains. Ransomware, on the other hand, just wants to cause as much damage as possible. It doesn’t need to encrypt all of your files to be successful - it just needs to scramble enough important ones. Ransomware grabs and encrypts anything: quarterly revenue spreadsheets, Word documents, PowerPoint presentations, generic README files, family photos. And the list goes on. Ransomware fires in all directions and hopes to hit something important. This lack of specificity makes ransomware more difficult to detect. You can’t concentrate on defending only certain locations or applications. You have to monitor everything, all the time.
Ransomware is alarmingly quick
Ransomware takes between five and 20 minutes to encrypt every relevant file on the average hard drive (depending on the speed of the machine and the number of files). That means that even the slowest, single-threaded ransomware can encrypt several potentially important files in seconds. Since ransomware works quickly, detection and response time is of the utmost importance, which may be problematic for certain behavioral-detection solutions. Unlike detection based on what the code is, detecting what the code does is prone to false positives and requires collecting additional evidence before a verdict is reached.
Every ransomware program goes over files, chooses the ones that look interesting, encrypts them and destroys the originals. You know what else does this? Compression software, legitimate encryption applications and backup and cloud-sync solutions in addition to many more programs. The same behavior is exhibited even if you manually compress a directory with a password and then delete it. Since ransomware encrypts any file anywhere on a computer, it’s extremely difficult to distinguish a legitimate file activity from a malicious one. While every encrypted file increases the likelihood that the ransomware will be detected, each encrypted file equals another important piece of information lost. Every second counts when ransomware starts encrypting files.
Cybereason RansomFree: Behavior - Based Ransomware Blocking Freeware
Cybereason researched more than 40 ransomware strains, including Locky, Cryptowall, TeslaCrypt, Jigsaw and Cerber and identified the behavioral patterns that distinguish ransomware from legitimate applications. Whether a criminal group or nation created the program, all ransomware functions the same way and encrypts as many files as possible. These programs can’t determine what files are important so they encrypt everything based on file extensions.
RansomFree, Cybereason’s behavioral anti-ransomware free tool, takes all these challenges into consideration. By putting multiple deception methods in place, RansomFree detects ransomware as soon as encryption occurs either on a computer or network drive. Once encryption is detected, RansomFree suspends it, displays a popup that warns users their files are at risk and enables them to stop the attack.
RansomFree protects against local encryption as well as the encryption of files on network or shared drives. The encryption of shared files is among the doomsday scenarios an organization can imagine. It takes only one employee on the network to execute ransomware and affect the entire company.
RansomFree catches stand-alone ransomware programs as well as fileless ransomware. Stand-alone ransomware uses vulnerabilities in applications, like buggy Flash code, but fileless ransomware abuses legitimate Windows tools, like the PowerShell scripting language or JavaScript, to carry out its malicious intentions.
You can download RansomFree now (it's currently available for Windows only), or share with friends and families. Try it out!