Large organizations are gradually starting to focus more on security awareness by enforcing strict protocols and implementing current security infrastructure and technology. However, implementing these policies, which are usually developed at corporate headquarters, in remote locations and business units remains a challenge.
This results in a more permissive approach to security at remote locations, which can greatly impact the entire organization. A permissive approach to software management and user behavior can allow potentially malicious programs to enter the organization, provide them with access to the company’s network, and result in an employee unknowingly allow attackers to compromise the business.
RAT with Permissions
Recently, Cybereason discovered suspicious software in the environment of a Fortune 500 customer. The software was legitimately purchased online and installed by the local help desk in one of the company’s remote locations to block user activity on social media.
The program, called Blok Supreme, is basically a remote administration tool (RAT) designed to do much more than that. The software can take full control of a host, akin to it having physical access to the system. As described on the website of the company that created the RAT, it's features include:
- Running in stealth mode and in Windows safe mode
- Complete remote access to the hosts on the network
- Application blocking
- Monitoring and filtering
- History log
The images below show what the RAT’s other capabilities. Blok Supreme’s features give it full access to a system.
Once installed, the RAT runs seemingly legitimate processes that use Windows OS names and descriptions, such as lssas.exe, and csrss.exe with the description of Processo do tempo de execução (“Runtime process”) and Local Security Authority Process.
Similar to classic malware behavior, all the executables of the RAT are saved under c:\windows\system32 and c:\windows\syswow64 with a randomly generated sequence of strings. For example:
- c:\windows\system32\wnba\csrss.exe
- c:\windows\system32\reslan\csrss.exe
- c:\windows\system32\tasksrv\csrss.exe
- c:\windows\system32\wsl2\lsass.exe
Some of the RAT’s executables are already known and identified by a number of antivirus programs (32\57 on VirusTotal) as malicious or as a potentially unwanted program. To circumvent this warning, the installation instructions note that some antivirus programs flag the program, but labels these notifications as false positives and directs users to disregarded them.
Blok Supreme’s installation instructions tell users to disregard any antivirus notifications.
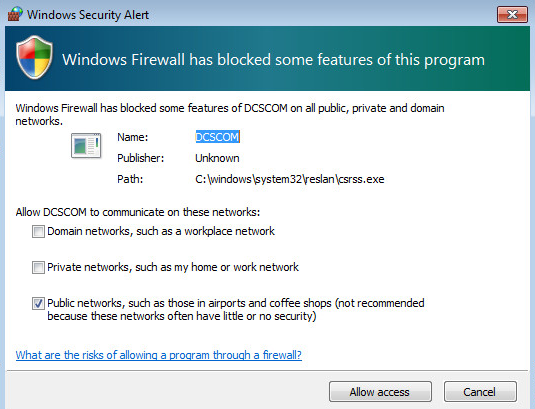
Windows Security alert
To maintain persistence, the RAT adds itself to the registry key HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell, enabling the program to automatically launch any time any user logs on to the host.
In addition, and for no apparent reason, the user is required to provide the administrator with an email address for contact upon installation.
Permission to Execute
What makes this RAT so interesting is that it appears to be legitimate and is signed and verified by the COMODO RSA Certification Authority. Blok Supreme can be easily downloaded from the developer's website as a trial version and later purchased for $46 per host.
The person who developed Blok Supreme is also behind five other programs that also perform remote administration control.
Recommendations
Although Blok Supreme’s behavior raised our suspicion and was flagged by antivirus programs and Cybereason, we didn’t see any indications of inappropriate activity. However, the tool has all the functionalities of a RAT and can be misused for illegitimate or malicious operations.
Cybereason recommends that companies implement security policies throughout all branches of the organization and ensure that these protocols are followed. Additionally, businesses should only download from software vendors that are industry verified and avoid installing programs from unknown sources, which can lead to security incidents.
Yana Blachman is a cyber threat intelligence analyst at Cybereason Labs.








