
Cuckoo Spear – the latest Nation-state Threat Actor targeting Japanese companies
In this blog, you learn about a highly sophisticated, well-funded, and strategically motivated nation-state cybersecurity threat called cuckoo spear.

Jacob Berry
In August, we hosted our first ever Cybereason Capture The Flag competition. While we intended to start small and grow, we had an impressive level of participation approaching almost 900 people! We had a blast building the challenges and interacting with all the participants, and hope you’ll join us for a future event!
We heard your feedback: More, More, MORE! We are working on the next iteration, so stay tuned for our next CTF announcement. Until then, here are some notes on the summer challenges to hold you over:
This was an enumeration JS script challenge. A web page of the Cybereason executive management team was provided. Clicking on each name provided a bio. As nearly all of the participants observed, our Chief Executive Officer was missing from the page. Modifying the ID=URL parameter to id=1 would provide his bio and the flag.
Malop
In this challenge, we asked participants to find the hash of a file that was used in a phishing attack. All that was provided was a machine name and login to the Cybereason Defense Platform. There were two ways to solve it using the provided Cybereason EDR instance.
Strategy One: Browse to Malops, where you investigate malicious operations, and select the phishing Malop. Scroll to the process section, and click investigate to see the Excel process details, along with the file that was opened.
Strategy Two: From Investigations, construct a query with the following logic:
Machine (Filter for Machine name) --> Process (Filtered for phishing suspicion) -> Files
Been There
This required using a dictionary brute force attack to find a password. A LSASS dump was provided. The intended path to the flag was to use Mimikatz to dump the LM Hash. Once you have the hash, crack the password using Hashcat and the best64 rule set.
Turns out, our google fu wasn’t fu -- some hash sites had the precomputed hash that you could search to find the password. Completely valid method, although this wasn’t intended.
In this network challenge, we provided a network service that could be connected to with telnet. When connected, a PIN prompt was displayed.
We recommend writing a script, such as in Python, to brute force the pin. This can be completed in a few lines in Python. Once a correct pin was entered (which was randomized on connection), a flag was output.
Swiftly
For this web log based challenge, we provided an hra file, a type of proxy or web transaction log. A vague description about RAID levels and the @SwiftOnSecurity Twitter account would lead you to find a transaction loading a tweet that implied, “Using RAID in place of a proper backup solution makes someone a clown.” (Their words, not ours).
And with some quick deduction, a flag of “clown” got points.
I'm Not Even Supposed to Be Here Today
In this analysis challenge, we asked participants to login to Cybereason and investigate a machine which we convicted earlier as being part of a phishing attack. The challenge was to identify the process that pulled down a command-and-control (C2) payload.
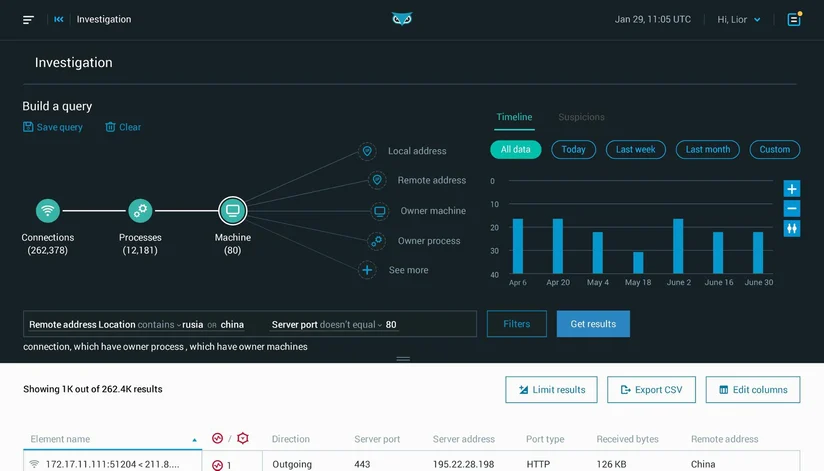
This was a tricky question. The attack spawned a child process to pull down a payload for C2. This stealthy technique was much less obvious than the first two stages of the attack.
Most people got the answer once they slowed down and analyzed the entire process tree associated with the phishing attack.
The second most talked about challenge! Participants needed to analyze a go lang binary in order to find the flag.
There are two ways to solve this:
“””
package main
import "fmt"
import "strings"
import "os"
import "bufio"
import b64 "encoding/base64"
func Password_Cat() string {
var flag string
flag = "Cyber"
flag = flag + "eason"
flag = flag + " Summer"
flag = flag + "X.X"
flag = flag + " CTF2020&01"
flag = strings.Replace(flag,"X.X","",-1)
flag = strings.Replace(flag, "2020", "", -1)
return flag
}
func Flag_cat() string {
var password string
password = "SWYgeW91IGNyYWNrZWQgdGhpcw=="
passwordDec, _ := b64.StdEncoding.DecodeString(password)
password = string(passwordDec)
passwordDec, _ = b64.StdEncoding.DecodeString("eW91IGFyZSBhIGdvb2QgcmV2ZXJzZXI=")
passwordDec2 := string(passwordDec)
password = password+" "+passwordDec2
password = b64.StdEncoding.EncodeToString([]byte(password))
return password
}
func main() {
fmt.Print("Enter Password: ")
user_input,_,err := bufio.NewReader(os.Stdin).ReadLine();
if err != nil {
fmt.Println("No input Detected")
}
if string(user_input) == Password_Cat() {
flag, _ := b64.StdEncoding.DecodeString(Flag_cat())
fmt.Println("Flag: "+string(flag))
} else {
fmt.Println("Well, that didn't work. Try Again")
}
}
“””””””
Are You Still Investigating That?
At this point, participants used Cybereason EDR to investigate the phishing attack. We asked participants to find the mobile device that connected to the same C2 server in the earlier CR challenge.
A query using our investigation screen allowed us to get this answer quickly. Filter for device type of Android or iOS, select the network relationship node, and filter for connections with a DNS query containing the C2 server.
Images != Password Vaults
The most discussed challenge! The solution is easy once you know it. This was a picture of a flag, with the picture metadata edited to have a smaller than actual pixel length in the header. The picture would display truncated.
There are a few ways to solve this challenge.
A Thin Pane of Glass
Finally, this was a Windows event log challenge. A security event log from a Windows machine was provided. One account had a login with a login type of 10, which denotes a remote interactive login. We asked participants which account was used remotely. Finding this account name was the flag. As an option, you could brute force or try all of the account names, but what’s the fun in that!
Capture the flag events are a highlight of working in the security industry. It’s a fun way to learn from each other, develop new skills, and make new friends along the way. We have been ecstatic to be able to join this part of the community, bring defenders together, and create a forum for learning. We will continue these, and similar types of events moving forward. Of course, if you have feedback please reach out. Being part of the community means listening to you!
Be sure to sign up to receive updates on our Winter CTF coming in February!

Jacob Berry, Director Sales Engineering at Cybereason, studied Cyber Security at Norwich University which instils a public service mentality. He has worked on extensive public sector security projects including a stint working for the Multi-state information sharing and analysis center (MS-ISAC). Today Jacob focuses on enabling the best security operations operators with the tools they need to combat the ever growing risk of the connected world.
All Posts by Jacob Berry
In this blog, you learn about a highly sophisticated, well-funded, and strategically motivated nation-state cybersecurity threat called cuckoo spear.

In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group’s new arsenal and techniques.

In this blog, you learn about a highly sophisticated, well-funded, and strategically motivated nation-state cybersecurity threat called cuckoo spear.

In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group’s new arsenal and techniques.
Get the latest research, expert insights, and security industry news.
Subscribe