1. DETECTION - going beyond prevention
“It's no longer about preventing attacks at the endpoint--that can't be done 100 percent of the time--but instead catching an attack or attack attempt ASAP. The goal is to mitigate the damage and stop any further infiltration into the network via the victimized user's machine. The goal is to mitigate the damage and stop any further infiltration into the network via the victimized user's machine.” Kelly Jackson Higgins, Dark Reading.
Our two core beliefs are:
1. Network penetration is inevitable
2. The post-penetration timeframe of the attack is the best window of opportunity for detection and interception of an attack
That makes detection a key for stoping advanced threats and APTs.
2. CROSS CORRELATION ACROSS THE WHOLE ENVIRONMENT
It is not enough to monitor each user or machine at a time to identify malicious behaviors. To detect advanced threats there's a need to automatically cross-correlate and query the whole endpoint and network environment. This is the only way to identify a hacker’s activity like privilege escalation, lateral movement, command and control communication, while differentiating it from abnormal but benign user activities.
3. Whitelisting and blacklisting are a good start
“When application whitelisting came on the scene a few years ago, it was touted as the answer to preventing malware from executing on a user's machine. But whitelisting--where only certain applications are authorized to run on the system and others are blocked--alone hasn't stopped attacks, just as host intrusion prevention system (HIPS) and host firewalls have not.” KellyJackson Higgins, Dark Reading.
In today’s security environment, whitelisting and blacklisting approaches should be used as a first line of detection to look for the known tactics hackers are still using. But there must be another layer that looks for new attack vectors since hackers constantly mutate the tools and methodologies they’re using to evade detection and blocking.
This is how we approach detection: whitelists and blacklist serve as a basis for detecting the attackers using known exploit kits and tools. But we don’t stop there. We use behavioral analytics to detect the tailored, new components of an attack.
4. Observing endpoints activity Without Interfering
“No one wants to burden the endpoint with heavy client software anymore: that was one of AV's biggest drawbacks.” Jackson Higgins, Dark Reading.
The endpoint component in EDR tools is key for enabling detection and response. Endpoint sensors are necessary for effective detection and response. It is key to have endpoint sensors that lightweight, non-intrusive and effective for continuous monitoring.
5. EMPOWERed Incident Response and Forensics
“Patient 0, the endpoint, holds valuable forensics clues and information, including malware footprints and other indicators of compromise. Gathering and storing that intelligence is key to getting to the bottom of an attack, as well as configuring systems to thwart a future one.” Jackson Higgins, Dark Reading.
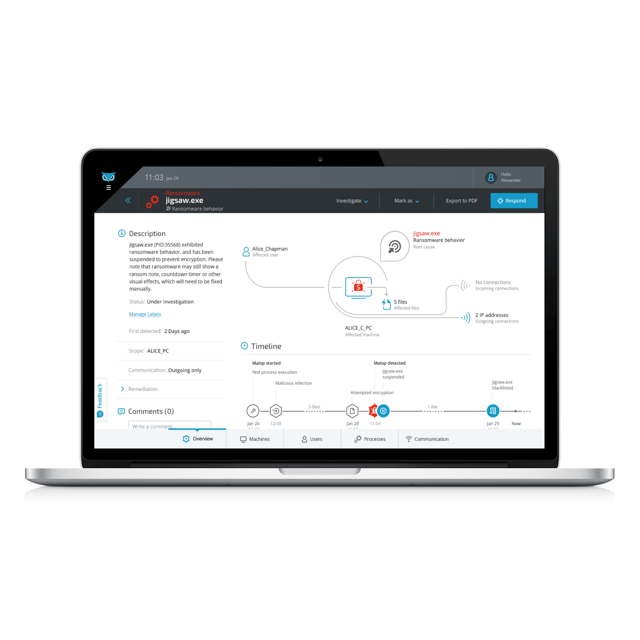
The advantage of EDR solutions is that they gather in real time every piece of information that would be relevant for incident response and forensics investigations: files, processes, hashes, user behaviors, authentication sessions and communication. Powerful EDR tools enable easy access to this data, providing immediate visibility to any area of the organization.
There’s an obvious need to significantly cut the time it takes from incident detection until the event is fully remediated. A key component is investigation time. Often, incident response teams have to gather forensic evidence from a variety of IT and security platforms and use this data to build a coherent attack story . EDR soultions do this automatically and present a coherent, visual attack story that includes the attack timeline, root cause, adversarial activities, affected users and endpoints and related communication.
6. Remediation and Cleanup
“Detecting and thwarting an attack's escalation is a big win, for sure, but if the victimized endpoint isn't properly cleaned up, patched, and reconfigured to fight another day, it may all be for naught.” Kelly Jackson Higgins, Dark Reading.
Effective remediation and cleanup are as good as the visibility the IR team has into the environment. EDR platforms are geared towards providing information to enable surgical, percise remediation plan.
7. working with your Antivirus. Yes, Antivirus.
“AV still does the job of catching everyday malware, which makes it tough to dismiss altogether.” Jackson Higgins, Dark Reading.
Yes it does. We agree. EDR is a great complement to blocking by AV. And when complementing a behavior-based NGAV: EDR is at its best.
.png)





