Cybereason Principal Security Researcher Amit Serper discovered a work around solution that disables the NotPetya ransomware that wreaked havoc in Europe in June 2017. To activate the vaccination mechanisms, users must locate the C:\Windows\ folder and create a file named perfc with no extension name. This should kill the application before it can begin encrypting files.
When first run, the NotPetya ransomware searches for its own filename in the C:\windows\ folder, and if it is found, will cease operating. Once the original file name was found and verified by two different sources, Amit was able to piece together a kill switch that should work for any instance of the original ransomware infection. Below is a series of his tweets that lead to the vaccination:
What is NotPetya?
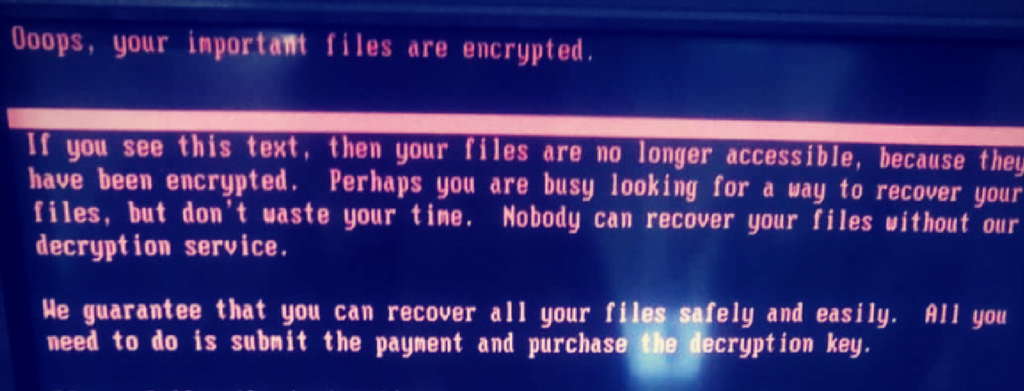
On June 27, 2017, a ransomware attack with similar functionality to Petya began infecting organizations across Europe. Dubbed NotPetya, the malware spread quickly across Europe and halted many organizations’ operations.
NotPetya was an untargeted campaign without a specific victim. Many of the impacted companies were infected after downloading a routine update for an accounting application that, unfortunately, attackers had tainted.
How did NotPetya work?
Unlike most ransomware that encrypt files upon execution, NotPetya encrypted files only after the machine was rebooted. NotPetya spread through networks, extracted admin credentials and scheduled a task to reboot the machine. As soon as victims rebooted their machines, the Master Boot Record (MBR) was overwritten with a malicious payload that encrypted the full disk.
The day after the attack, the Cybereason Intelligence Group posted a quick recap that covers initial attack details and explains why NotPetya was unique. If you are interested in the attack’s intrusion vectors and propagation, check out the Intelligence Group’s flowchart infographic.
What was the impact of NotPetya?
The primary goal of most ransomware attacks is to make money, but NotPetya’s goal was to cause as much disruption as possible. On that front, the attack succeeded: offices closed, people were unable to buy food at supermarkets and employees were told not to use their computers.
In the months following the attack, global organizations began attributing significant losses to NotPetya. Some examples include shipping giant FedEx, drug maker Merck, software vendor Nuance Communications and food and beverage company Mondelez International. Cybereason first calculated that NotPetya cost companies a total of $592.5 million in quarterly and yearly revenue, but that figure exceeded $1 billion by November 2017.
Does Cybereason detect NotPetya?
Yes. Cybereason collects and analyzes behavioral data to identify if and when malicious activity occurs in an environment. In the case of NotPetya and other MBR-based ransomware, the product detects malicious activity that attempts to affect the MBR. If a machine is infected with NotPetya, Cybereason will detect the activity and block NotPetya from encrypting any data. An infected machine will still need to be rebooted, but Cybereason will restore the original MBR and prohibit NotPetya’s from succeeding.