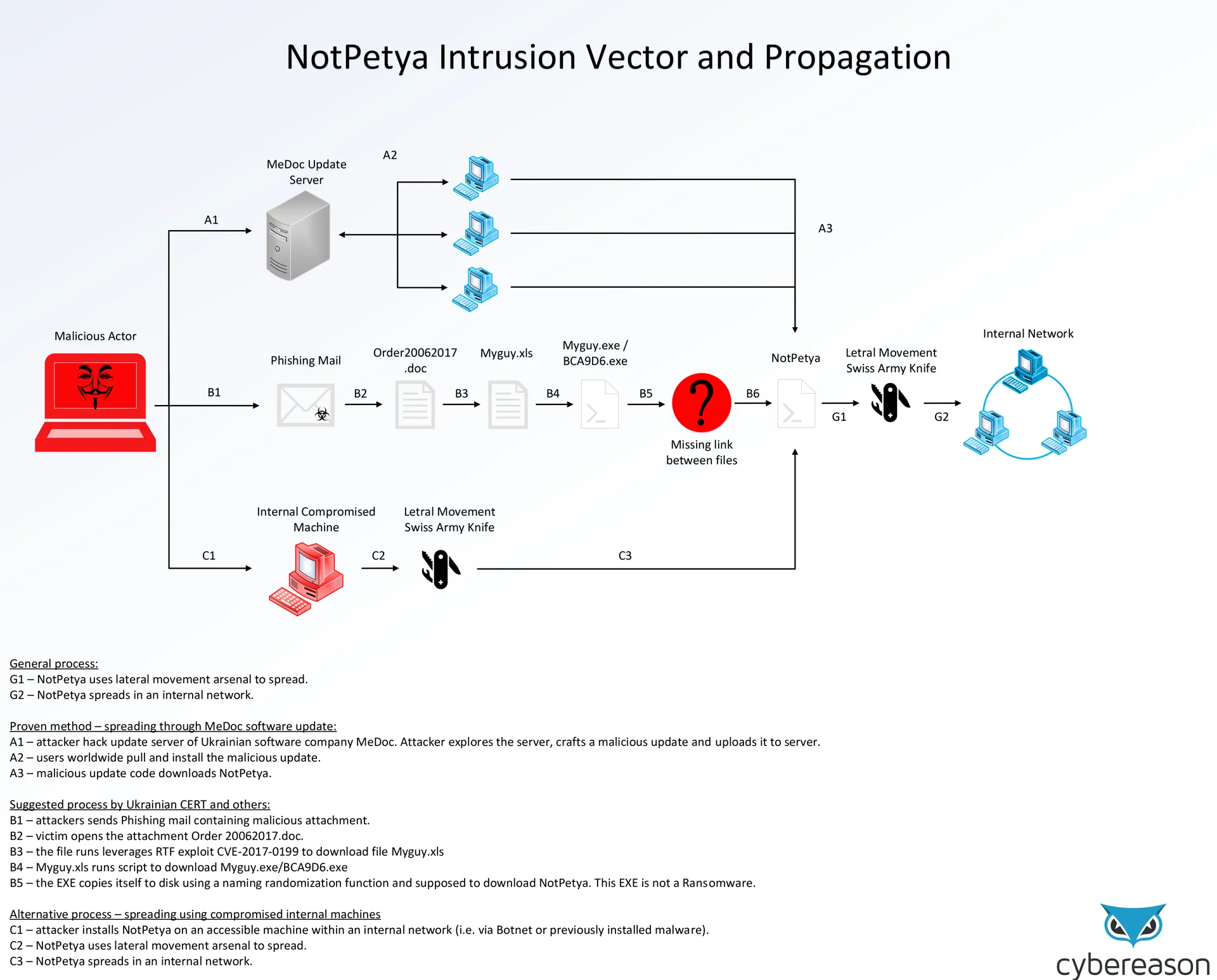
The Cybereason Intelligence Team has created a flowchart mapping out the intrusion vectors and methods the malware might have taken to infect up to 12,000 endpoints, the majority of which in Ukraine. Intrusion vectors are the ways by which the NotPetya files might have gotten onto the compromised networks and computers.
Medoc
There are a few possible vectors the malware might have taken. Out of the three, the only one we have the most amount of information on is the MeDoc Update Server method (illustrated by vector A).
MeDoc is a Ukrainian software provider whose servers have been compromised prior to the attack. The attackers leveraged their access they gained to add the NotPetya files to the servers that deliver automatic updates to the users of MeDoc’s software. In this way NotPetya was able to spread by disguising itself as a legitimate update to MeDoc’s software. Users had very little reason to suspect that this most recent update was out of the ordinary.
Luckily, this is a relatively uncommon intrusion vector, but not unheard of- the Monju power station in Japan, for example, was compromised via an update to a video playback program.
Phishing
Some are pointing towards a phishing campaign as the intrusion vector (vector B), primarily the Ukrainian Computer Emergency Response Team, that was asked to assist in the early hours of the infection.
In their inspection, they report finding phishing emails containing a malicious program called Myguy. It is believed that perhaps the Myguy malware, once it infected a computer, downloaded the NotPetya malware as well. This hypothesis has not yet been fully confirmed.
Alternative methods
While most evidence currently point towards vectors A and B, we cannot rule out for sure the existence of any alternative infection vectors, such as purchasing access to a computer already compromised, or infecting a computer with a relatively benign malware first, and later having it download the NotPetya malware. Due to NotPetya’s robust array of lateral movement tools, it is able to spread from one computer to the entire network in a short amount of time.
Lateral movement
Movement between computers in a computer network, also known as lateral movement, is accomplished in several ways:
- The EternalBlue exploit- this is the same exploit used by WannaCry
- The EternalRomance exploit- a second exploit from the ShadowBroker dump
- PsExec- a hacking technique known as Pass the Hash
- Windows Management Instrumentation- a tool used by network managers that was exploited by the NotPetya to spread within the networks it was present in
- Mimikatz- a Metasploit module used to collect passwords in order to establish a remote connection within a given network






