Last week Cybereason observed a massive wave of infections to crypto-currency botnets in the environments of multiple Japanese customers. The payload was delivered through the DoublePulsar exploit, as previously reported by Proofpoint researchers. DoublePulsar uses a vulnerability in Microsoft Server Message Block (SMB) to locate unpatched computers on a network and laterally disseminate malicious payloads. Microsoft issued a patch for this exploit on March 14, 2017, in security bulletin MS17-010.
Our data shows that the crypto-currency miner Adylkuzz exploited this vulnerability before the WannaCry ransomware leveraged it last week to infect 200,000 Windows machines in 150 countries, further confirming what other researchers have already shared. This post will look at how Cybereason detected the Adylkuzz crypto-currency botnet using the DoublePulsar exploit.
DOUBLEPULSAR delivering Adylkuzz
Cybereason observed incoming connections towards PID 4’s (“system” in the Cybereason platform) listening port 445 from unfamiliar remote locations:
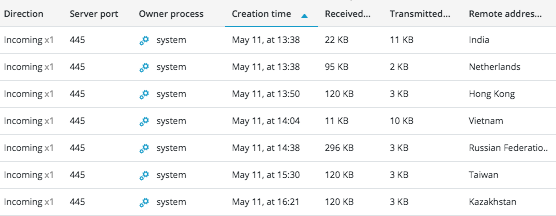
Incoming connections over SMB observed attempting to deliver DOUBLEPULSAR
The payload delivering the crypto-currency botnet was executed immediately after the end of the incoming connection, which confirms the use of the DoublePulsar exploit.
The exploit infects a legitimate Windows service and runs a downloader to fetch the payload.
Below are details of the infected service, resolved DNS queries, and the connected IPs.
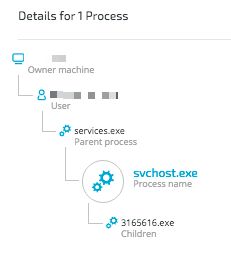

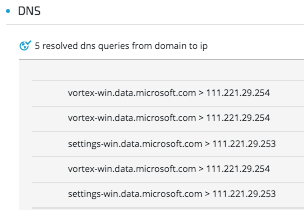
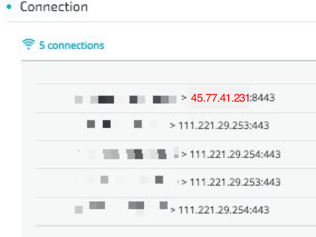
The above data collected by Cybereason shows that the DOUBLEPULSAR backdoor downloaded the Adylkuzz botnet, using svchost.exe (Diagnostic Tracking Service) directly from 45(.)77.41.231.
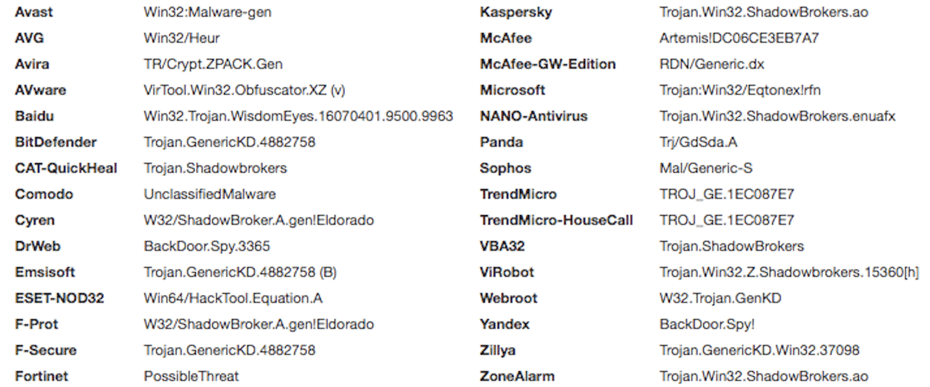
While examining this IP address, we noticed that it is linked to ShadowBrokers / Equation payloads that were detected by multiple antivirus vendors.
https://virustotal.com/en/ip-address/45.77.41.231/information/
https://virustotal.com/en/file/b704dd388be29de7a33e2a806dc1dfb391a8f22f0b8f5f4c858f9fcf18455288/analysis/
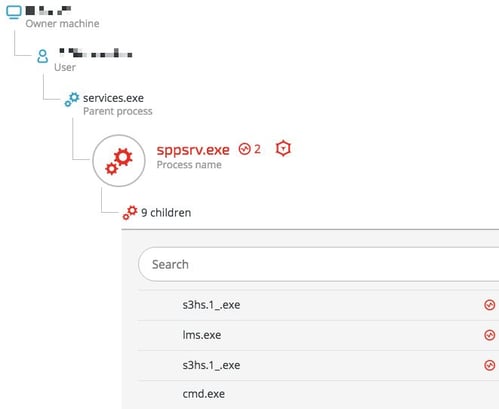
The Adylkuzz botnet execution
Once downloaded and installed by DOUBLEPULSAR, the Adylkuzz botnet runs as a service (sppsrv.exe) with SYSTEM privileges and takes the following actions:
- Check internet connectivity using a known IP service
- Communicate with Adylkuzz C&C server
- Downloads the Monero cryptocurrency miner and additional tools
Monero Crypto Currency Miner
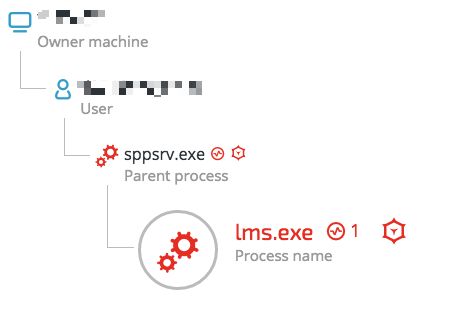
lms.exe - c3fbd25209ca8aff4a50106226713afc3c970143
The lms.exe process is responsible for the Monero cryptocurrency mining, as can be seen in the command line:
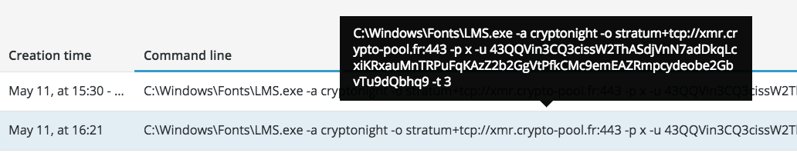
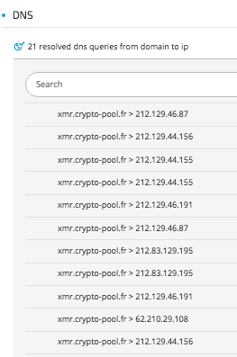
DNS requests made to the Monero mining pool server:
Adylkuzz executes additional tool and commands:
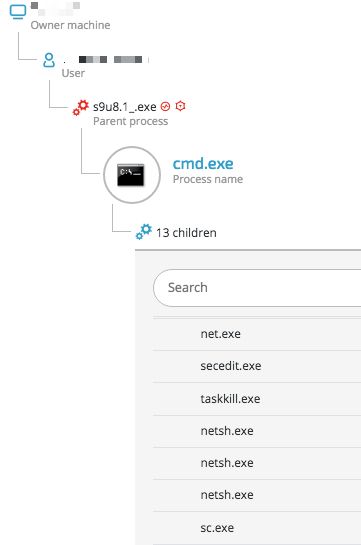
Adylkuzz will also download an additional tool (s9u8.1_.exe - e40811db66973dd7d2be2f5eb5d5f0ed824a1a3b) that runs a long series of commands. This includes commands that ensure that the malware won’t have any “competition” coming from potential additional infections originating from the same SMB exploit. This is done by creating a Windows firewall rule that blocks connections running on port 445 (default SMB port):
.png?width=529&name=image11%20(2).png)
Observed binary files
| File name |
SHA-1 hash |
| sppsrv.exe |
b152473428e0eb7c372e59e6978fcc69c30975b6
d2dac771a08d1826354a5d5728cbecf714d386c8
|
| lms.exe |
c3fbd25209ca8aff4a50106226713afc3c970143 |
| s9u8.1_.exe |
e40811db66973dd7d2be2f5eb5d5f0ed824a1a3b |
Observed domains and IPs
g.disgogoweb.com > 104.24.120.122 (Adylkuzz C&C server)
xmr.crypto-pool.fr > 212.129.46.87 (Monero Crypto Pool Miner)
icanhazip.com - checking internet connectivity and geo-location















.png?width=529&name=image11%20(2).png)

