Malicious Life Podcast: The Roots of Evil: Ransomware, Pt. I Transcript
Hello, and Welcome to Malicious Life. My name is Ran Levi.
Friday, May 12th, 2017 was a bad day for quite a lot of people. In over 150 countries, businessmen, doctors, bankers, and technicians turned on their computers – and instead of their regular desktop, they got a big red window with a big white lock drawn on it, and the words:
“Oops, your files have been encrypted!”
And indeed, the files on the computer were unreachable. Under the lock were a timer and a notice demanding 300$ in Bitcoin. If the sum was not paid before the timer ran down – the files on the computer would be lost forever. The name of the ransomware was WannaCry.
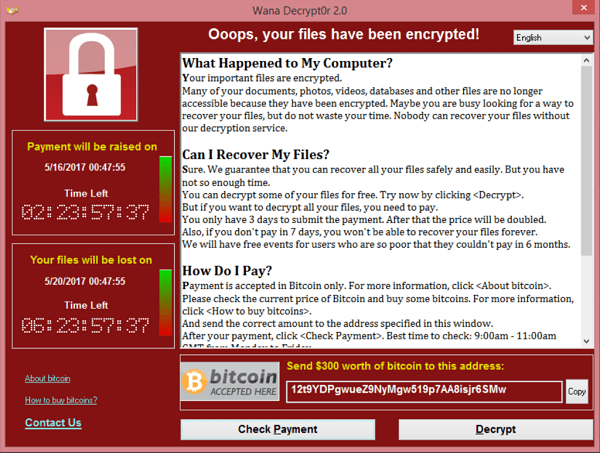 Wannacry Screenshot
Wannacry Screenshot
WannaCry’s widespread cyber attack on more than 200,000 computers all over the world made headlines in the media and brought the issue of ransomware into the public eye. But only a few people remember that almost 30 years ago, on December 1989, a few thousand people woke up in the UK and several European countries to discover a very similar scenario. Upon turning on their PCs, the following message appeared on the screen:
“Please wait 30 minutes during this operation. WARNING – do NOT turn off the computer because you will damage the files on the hard disk drive.”
After a tense 30 minutes, the users received another worrying message:
“The software lease for this computer has EXPIRED. It is time to pay for your software lease from PC Cyborg Corporation. The price of a lease for the lifetime of your hard disk is US$378. Mail your order to PC Cyborg Corporation, P.O. Box 87-17-4tl Panama.”
All the files that were stored on the hard disk were gone. When the users tried rebooting their computer, they received the same message again and again. Although the word ‘extortion’ didn’t appear anywhere, the subtle threat could not be missed.
A White Envelope
Reports of the ransomware began flooding police stations. It didn’t take long to find the common denominator: all victims received per post a few days earlier a white envelope containing a floppy disk. The envelope was sent from the PC Cyborg company. The disk was labeled:
“AIDS Information Introductory Diskette Version 2.0”
The adults among us probably remember that during the 80s and the 90s it was quite common to receive disks and CDs per post. They were usually attached to magazines and contained freeware and demos. Furthermore, a few thousands of those who received the envelope participated in that year’s convention of the World Health Organization on AIDS, so they weren’t surprised to receive a disk on that subject. Either way, many of the recipients actually installed the software on their computer. They weren’t disappointed: the software did provide them with useful information. It presented a short questionnaire concerning age, ethnic heritage, sexual habits and other topics, and then analyzed their risk of contracting AIDS. There was no reason to suspect that hiding inside the software was a ‘Trojan horse’: a malware masquerading as a legitimate software.
Along with the floppy disk, the envelope contained a blue sheet of paper with instructions for installing the software, and a license agreement. The agreement seemed like a standard legal contract, the type that most of us would skip over while installing a software, but the few users who did bother reading it discovered that the agreement’s terms dictated that installing the software actually constitutes purchasing it:
“There is a mandatory leasing fee for the use of these programs; […] they are not
provided to you free of charge. If you install these programs on a microcomputer […] then under the terms of this license you thereby agree to pay PC Cyborg Corporation.”
These terms are highly irregular in the world of computers – but that wasn’t the end of it.
“In the case of your breach of this license agreement, PC Cyborg Corporation reserves the right to […] to use program mechanisms to ensure termination of your use of the programs. You are hereby advised of the most serious consequences of your failure to abide by the terms of this license agreement; your conscience may haunt you for the rest of your life.”
Most users were more concerned with their files than their conscience, and information security experts hurried to analyze the ransomware. Despite the ominous first impression, the trojan itself was relatively unsophisticated. The files, it was discovered, were hidden inside invisible folders inside the computer, and their names were encrypted in a way that turned them into meaningless gibberish- but the way in which they were encrypted seemed amateurish. The encryption was a simple switch of the characters: for example, the letter B was switched with the letter U, the letter F with an exclamation mark and so on. The researchers examining the code easily traced the switch table and within days, a new software was created to remove the ransomware and bring back the files to their original state.
A Weird Crime
The Scotland Yard opened an investigation. They discovered that PC Cyborg was a straw company founded in Panama a few months earlier by 3 gentlemen with seemingly African names: Kitain Mekonen, Asrat Wakjira and Fantu Mekesse. The addresses for their offices in Panama and in London were fictitious, nothing more than mail boxes. The envelopes were sent to roughly 10,000 addresses: 3,000 of them participated in the WHO AIDS convention and 7,000 were subscribers of the PC Business World magazine. The mailing list was purchased from the newspaper by a man named Mr. Ketema.
The police officers and information security experts examining the case were confused. Were they facing an international, well-organized gang of sophisticated criminals? The straw company and method of extortion suggested great sophistication and required a serious financial investment. The floppy disks alone must have cost several tens of thousands of dollars. On the other hand, the ransomware itself was amateurish, and the phrasing of the license agreement was simply…weird. In a report regarding the ransomware, published by three security researchers- Dr. Alan Solomon, Barry Nielsen, and Simon Meldrum, they wrote:
“It is difficult to take this diskette at face value. […] In the light of the careful preparation of this diskette, and the large sum of money spent, it is surely not possible that the crude attempt at blackmail (if that is what it is) is the only outcome.
Is it possible that we haven’t heard the last from PC Cyborg? Is it possible that in several weeks time, we will get another letter which is the real ransom note? […] On the other hand, is it possible that we are dealing with simple crackpots? If so, there may be no motive, and what we have seen is all there is.”
Two weeks later, a breakthrough in the investigation occurred. At the Amsterdam airport, Dutch police detained a man that was acting in a peculiar manner. His name was Dr. Joseph Lewis Papp, a 39-year-old American expert on anthropology who was conducting research on apes in Africa. He was on his way back from Africa to the US, but was displaying paranoid behavior: he complained to the police officers that someone was trying to kill him, and even scribbled on the luggage of another passenger- “Dr. Papp was poisoned”.
The officers examining Papp’s luggage discovered among his belongings an ink stamp with the writing ‘PC Cyborg’. The Dutch police reported their finding to the Scotland Yard and released Dr. Papp to continue his flights to the US. The FBI and Scotland Yard began an undercover investigation of the scientist.
A Brilliant and Calculated Man
The investigation showed that in the years prior, Dr. Papp developed a special interest in the HIV epidemic, and even organized a special convention on the topic in Kenya- but shortly before returning to the US, he was fired from his job at the World Health Organization. He lived with his parents in a small town in Ohio, and his neighbors described him as a quiet and pleasant man. After 3 months of undercover investigation, the detectives arrested Papp. In a search of his house, they discovered about a million empty disks. He was apparently planning to use the profits from the first extortion to finance a second wave of ransomware to new victims.
Joseph Papp was extradited to England, which was where most of the damage was done as a result of his ransomware, and stood trial. He admitted to sending the software but claimed that it wasn’t a premeditated attempt at extortion. After all, he had clearly written in the license agreement that installing the software entails payment, and refusal to pay would damage the computer. It’s not his fault that the users didn’t read the license agreement! Unfortunately for him, the court rejected his (ridiculous) claims.
The trial also revealed Papp’s motive- he claimed that the WHO and African governments were conspiring to prevent information regarding HIV from reaching their citizens since the lethal epidemic was an effective means to prevent population growth. His plan was to use the money earned by the ransomware in order to perform independent research and expose to the public the dangers of HIV.
Papp was a brilliant and calculated person, there was no question about it. For example, he made sure not to send the infected disks to users within the USA, so as not to stand trial there. But Papp’s conspiracy claims and his megalomaniacal plan only made the judges more certain that he was mentally ill. Furthermore, he would appear to court wearing cardboard boxes on his head and curlers in his beard, to protect himself against ‘lethal radiation’…eventually, the prosecution agreed to acknowledge that Dr. Papp was a ‘public disgrace’: a legal status allowing to finish the trial without a conviction. Papp was returned to the US where he spent the next few years in a mental hospital.
Not much is known of Papp after the trial. He moved to New York, published a not very good book titled Popular Anthropology, and founded a butterfly conservatory in his name. He was killed in a traffic accident in 2006.
There’s no doubt that as far as crime schemes go, the AIDS Trojan turned out to be a total flop. Papp spent tens of thousands of dollars buying the disks and founding his straw company, but the security researchers who cracked his code made quick work of it, and none of his victims had ever sent even one cent to his address in Panama. In fact, that AIDS Trojan was such a colossal failure, that it took more than 15 years- almost an eternity in computer terms – until someone in the underworld decided to give the idea of computerized extortion another try. But that doesn’t mean that the AIDS Trojan didn’t have any effect on the computer world. Quite the opposite- it would be correct to say that because of Dr. Papp’s echoing failure, we were able to “enjoy” more sophisticated and successful ransomware in WannaCry.
A Cryptographic Attack
Dr. Moti Yung is an American-Israeli computer scientist from Columbia University, and a renowned expert in the field of Cryptography- the study and implementation of encryption techniques. In 1996, he joined another researcher from Columbia University, Adam Young, to found a new field in Cryptography: Cryptovirology.
Dr. Moti Yung - Malicious.Life Podcast
Dr. Moti Yung
What is cryptovirology? Well, traditionally, cryptography examines ways to protect information from an adversary, through its encryption: for example- developing hard-to-crack codes to be used for transferring secret messages to spies. Cryptovirology, in this context, is interested in developing ways to attack the adversary using encryption – such as preventing the adversary from accessing vital information. It is the exact opposite of what classical cryptography would usually try to do.
The inspiration for this field of study came following the huge tide of computer viruses in the mid-80s and early 90s, and especially those attacks that were cryptography based, such as Dr. Papp’s. In a 1996 article entitled “Extortion-Based Security Threats and Countermeasures”, the two researchers examined the AIDS Trojan and other similar viruses. Their main conclusion was that the AIDS Trojan suffered from a basic weakness because of the type of encryption it used: a ‘symmetric’ encryption.
To understand symmetric encryption, consider a typical door key- one turn of the key locks the door, and a turn in the opposite direction opens it. That’s how symmetric encryption works: the same key is used for encrypting and decrypting the code. Remember the switch table that Papp used for the AIDS Trojan? The table defined that the letter B will be switched by the letter U, and the letter F by an exclamation mark, and so on. The table is symmetrical, or bi-directional, since it can be used in both directions, switch U with B and ! with F.
This type of weakness has to do with what the ransomware does with the key after it finishes encrypting the files. The criminal promises his victims that if they pay the ransom, he will release their files. Therefore, the virus must keep this key somewhere in order to be able to decode the files after the payment. The researchers who analyzed the AIDS Trojan were aware of this fact: that’s why they kept looking until they found the table inside the ransomware’s code, which is the cryptographic equivalent of hiding the key under the doormat. In other words, symmetric encryption is vulnerable because it’s hard to hide its key.
Moti Yung and Adam Young found a way to overcome this weakness and to make ransomware like the AIDS Trojan much more difficult to crack. Their solution is based on the so-called Asymmetric encryption, which can be equated to a lock that has 2 keys- one that locks the door and another one that unlocks it. The locking key, the one that encrypts the information, is called the Public Key, while the other one, the one that decrypts it, is the Private Key.
The technique that Jung and Young offered is this: the criminal, the one who is writing the ransomware, creates two keys. He places the public key in the ransomware and keeps the private one to himself. When the ransomware takes over a victim’s computer, it encrypts the files on it with the public key- meaning it “locks” them. The fact that the public key is in the ransomware’s code, visible for everyone to see, changes nothing: the only key that can decrypt the locked files is the private key, which only the criminal has, and will release it only in exchange for the ransom. That is the principle behind the idea, and the two researchers expanded on it in their article, in order to make it more robust in real world conditions.
An Ethical Dilemma
This is a good place to say a few words regarding the ethical dilemma that Jung and Young were facing when publishing their article. They knew full well that their article would reach the hands of criminals, and they were right: granted, it took about a decade from the publication of the article until the first ‘modern’ ransomware appeared in 2005, but many of them indeed used the asymmetrical encryption suggested by the authors. There were those who wondered aloud why the scientists would provide such a valuable ‘gift’ to criminals in the form of a technique that would make their ransomware more dangerous and harder to crack. Would we have been understanding towards a weapons expert that gave a potential murderer tips on how to aim his weapon? Young and Yung, who were very mindful of this dilemma, explained their motives in the first paragraph of the article:
“Every major technological development carries with it a certain degree of power. This power is often beneficial to society, but more often than not it can also be severely misused. […] Cryptography is a blessing to information processing and communications because it allows people to store information securely and to conduct private communications over large distances. It is therefore natural to ask, “What are the potentially harmful uses of Cryptography?” We believe that it is better to investigate this aspect rather than to wait for such attacks to occur.”
In other words, the two researchers consider cryptography a neutral technology: one that could benefit the public but just as easily harm it. It is clear to them that even if researchers ignore the harmful potential of technology, criminals will not. Therefore, it would be better if researchers were one step ahead of criminals, identified the harmful uses of the technology and prepared appropriate defenses against such uses. In this respect, Yung and Young faced the same moral dilemma as many other scientists throughout the 20th century, in topics such as the development of nuclear energy and nuclear bombs, chemical and biological weapons, and so on.
A Negligible Threat
As already mentioned, ransomware came back to the forefront of technology around 2005, equipped with more advanced encryption techniques than that used by the AIDS Trojan. Ransomware such as GPCoder, Archiveus, Cryzip and others started terrorizing computer users, especially in central and eastern Europe.
Despite this, if we examine the overall map of cyber threats in the first decade of the 21st century, we will see that ransomware was still a negligible threat when compared to other cyber-crimes. Only a few ransomwares were discovered throughout the years, compared to millions of other malware being discovered monthly. It would seem that despite the precious gift given to them by Yung and Young, the execution of a successful extortion campaign was still a challenge that only a few criminals could carry out. Why? Because cryptography is one of the most complex and challenging fields of computer science. There is a difference between an understanding, even a good understanding, of a certain cryptographic idea, and putting that idea into practice. Any error in the encryption algorithm, even the smallest one, opens a way to cracking the code- and information security researchers are experts at finding these cracks in the codes of malwares. Ransomware is a good idea on paper, but most cyber criminals preferred picking the lower hanging fruit and settled for spam, DDoS or other types of computerized crime.
Those criminals who did find extortion attractive turned their efforts to another, more easily applicable types of ransomware. These were called Lockers, and they didn’t encrypt the files on the computer, but simply prevented the user from accessing them. For example, a malware called Reveton would display a big image on the user’s screen with the logo of the local police department, along with a message saying that the software identified pornographic files or other illegal contents on the computer. The big image could not be closed and prevented the user from clicking on icons and operating other software until a fine of 100 Euros was paid. Other ransomware used similar tricks such as popping up a message that emulated the paid activation dialogue for the operating system, opening a web page that can’t be closed and so on. Luckily, these lockers were not very successful, either: many users were able to overcome these locks without paying the ransom.
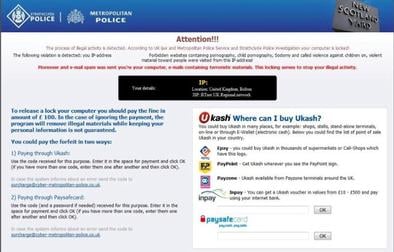 The Reveton Locker Scam
The Reveton Locker Scam
The Monetization Problem
Another reason for the lack of popularity of ransomware among criminals, other than the difficulty in applying good cryptography, is another problem that Joseph Papp had to deal with back in 1989, and that is monetizing. In other words- how do you take money from your victims without the police tracking you down, and without the victims canceling their payment immediately after getting their files back? It’s not easy since money tends to leave a ‘trail’ of receipts, verifications and similar documents, eventually leading to the criminal. Joseph Papp tried to cover his trail by establishing a straw company in Panama that would cash the checks that victims send- but he failed miserably when he was caught with the PC Cyborg ink stamp among his belongings.
Uri Sternfeld is a lead researcher at Cybereason and develops defense software against ransomware. He fully admits that when he first encountered the ransomware phenomenon, he was skeptical of its chances to succeed, mainly due to the monetization issue:
“[Uri] So usually what they did in the past years before the ransomware phenomenon was either to steal bank account numbers and passwords or credit card numbers. In order to do that, you need a very substantial criminal infrastructure outside the cyber world. You need…
[Ran] Money mules?
[Uri] Money mules, money laundering. You need the people all around the world who can pull money from ATMs, small amounts at a time and then transfer them to you. It was really hard work, and it was basically only available to really big and organized crime organizations. So, the idea that someone will willfully want to pay a ransom was ludicrous, because when stealing bank account number or a credit card number you basically have a very short time window during which you can steal money. And since banks are so good at detecting fraud and stolen cards then usually they contact the person and they say, “Hey, we think your card was stolen.” Then, they cancel the card and you have to move on to the next victim.
So of course if a victim discovered that his credit card was compromised then the first thing that you do is they will drop everything and call the bank and cancel the card. The idea that someone will agree to pay the ransom on their own accord and transfer money directly to criminals without canceling it immediately after was simply ludicrous. So the reason they failed was that it was almost impossible to monetize them in a way that is both sustainable and untraceable.”
The creators of 21st century ransomware tried various methods of dealing with the monetization challenge. The ransomware Archiveus, for example, demanded from its victims to purchase certain medications in an online pharmacy in order to release their encrypted files. The ransom, in this case, was the commission that the ransomware’s owner earned for the purchase. Another ransomware named WinLock forced users to send an SMS to a premium number, the cost of which was 10 USD. Others used electronic money transfer services such as E-Gold, or anonymous cards that could be charged with cash. Each of these methods had its disadvantages: some were too easy to trace, others susceptible to payment cancellation by the victim and more.
The Rise Of Ransomware
All this changed in 2008, when an anonymous web surfer, hiding under the alias Satoshi Nakamoto published in one of the forums an article offering to establish a new virtual currency called Bitcoin. Shortly thereafter, Nakamoto released a software which implemented his proposal and launched a website dedicated to this endeavor. Bitcoin’s financial revolution is still underway – but the results of another revolution that Nakamoto generated- most likely unintentionally- can already be seen: the rise of ransomware.
How did BitCoin cause ransomware to turn from a negligible threat to the most common and dangerous cyber-crime of our time? This will be the topic of our next episode. We will hear about CryptoLocker, one of the most dangerous ransomware in history, and about the Russian hacker who created it, thus becoming one of the FBI’s most wanted, with a $3 million bounty on his head. We will also discuss the future of ransomware in a world of autonomous cars and smart houses. All this and more in our next episode.








 Wannacry Screenshot
Wannacry Screenshot The Reveton Locker Scam
The Reveton Locker Scam