
When Your EDR Vendor Attacks!
SentinelOne's use of PowerShell in their product is similar to how malicious actors abuse it, causing False Positives for customers and an uproar on Twitter...
Paul Stamp
ZDNet recently published a really good article on the Panama Papers. The article talks about how analysts used graph database technology to analyze transactions and identify all manner of financial jiggery-pokery made to look cleaner than a clergyman’s conscience.
The graph database is a really interesting technology, and is at the core of Cybereason’s Malop Hunting Engine. A graph database uses nodes, edges and properties to represent data and, more importantly, the relationships between them.
In the case of the Panama Papers this was really useful, since once analysts could identify a transaction or a customer they knew wasn’t kosher, they could pick apart the relationships between that bad apple and all the people they did business with. If someone engages in one dodgy transaction, then there’s a higher probability that other transactions they’ve conducted and the people they’ve done business with are dodgy too.
In the same way, every element that Cybereason collects - all the users, machines, processes, network connections and auto-runs - and the relationships between those elements gets analyzed in the graph. This way, once we spot something we know is bad, we can quickly pull on the different loose threads and get a bigger picture of all the other bad things that might be happening.
What’s more, nodes get continuously added as more and more data is fed into the graph, and more relationships get established. This turns the Hunting Engine into an ever-evolving, in-memory, real-time picture of your environment.
Paul Stamp is the Director of Product Marketing at Cybereason.
Paul is the former Director of Product Marketing at Cybereason.

SentinelOne's use of PowerShell in their product is similar to how malicious actors abuse it, causing False Positives for customers and an uproar on Twitter...
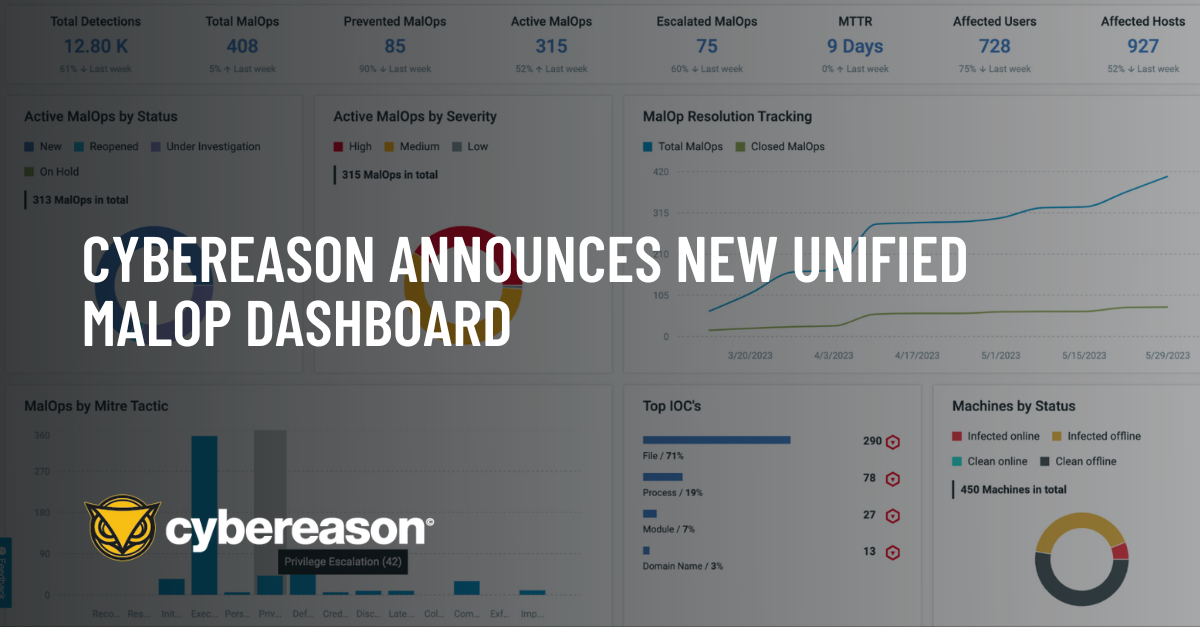
To help SOC teams stay ahead of the curve, Cybereason introduced a unified dashboard designed to provide additional insights into emerging threats, operational metrics and provide insights to continuously improve SOC processes and procedures.

SentinelOne's use of PowerShell in their product is similar to how malicious actors abuse it, causing False Positives for customers and an uproar on Twitter...

To help SOC teams stay ahead of the curve, Cybereason introduced a unified dashboard designed to provide additional insights into emerging threats, operational metrics and provide insights to continuously improve SOC processes and procedures.
Get the latest research, expert insights, and security industry news.
Subscribe