
Malicious Life Podcast: Hacker Highschool
Pete Herzog, co-founder of ISECOM and Hacker Highschool, wants our kids to learn about cybersecurity - especially the more advanced stuff like security analysis and hacking - check it out...
Lital Asher-Dotan
Co-Authors: Amit Serper and Alex Frazer
With the public release of the Hacking Team’s secrets, our researchers took advantage of the ability to dig deeply into the minds behind their operational theater. For security researchers this information is a veritable gold mine, providing us with even more clues into the latest techniques and tactics hackers are using, and how easily they are able to maintain their attacks over time. Two of our security researchers recently sat down to examine the available data, and found some amazing details about Hacking Team's activities, victims... and even the hackers that in turn brought them down.
This data dump is akin to the fall of the Soviet Union in a way. When the U.S.S.R. fell, global black markets were overflowing with Soviet weapons and, more importantly, knowledge of WMDs. This put more sophisticated weaponry and nuclear capabilities in the hands of the highest bidder, much like the Hacking Team leak has done. Except in this case the information is free, and none of the vendors whose products are exploitable, e.g. Adobe and Microsoft, were notified, amplifying the danger of the leak.
The widespread availability of this data is going to empower hacking teams across the globe, providing them with much more sophisticated techniques to launch their own attacks. These newer operations will have a completely different signature than Hacking Team’s efforts, but because of how detailed the information on their delivery server is, with perfectly readable code and extremely detailed comments, we can assess the behavior these attacks will follow and more accurately and quickly identify these operations in the future.
What we want to look more closely at is how Hacking Team targeted their attacks, and the techniques they used to maintain such large-scale operations over extended periods of time.
Hacking Team used a particular ingenious strategy for gaining access to victim machines. Firstly, the team’s operations mirrored that of the Flame malware discovered in 2012. Flame’s C&C server interface mimicked a news and adwords service, offering its “customers” - the term they used to refer to targets - a link to an “ad hosting” server, which then installed the malware. Many of its commands and protocols used news-related jargon to continue to fool detection tools and security analysts, and Hacking Team’s tactics followed the same strategy.
In fact, on Hacking Team’s delivery server, we found a base64 binary file titled “news,” which we discovered was their payload. When we de-scrambled the base64 file, we found a big data blob - an AES encoded binary - containing a multi-staged payload that runs a zero day exploit for privilege escalation. The payload then executes Hacking Team’s Remote Control System (RCS) agent, which is padded with random binary data, a common anti-virus avoidance tactic.
Using a variety of standard and new techniques, such as phishing and watering hole attacks, potential targets would receive a link. Once the recipient clicked on the link, the infection server would immediately assess whether or not the machine was, in fact, a targeted recipient. If not, the script would automatically redirect them to a 404 error page or another homepage - something news or ad related (customer configurable) so as to not arouse suspicion. However, if the clicker was the intended target, the server would then profile their machine to determine their OS and browser. The server would then be able to determine if the target is using IE, Firefox, or Chrome, and what operating system they’re running, and then leverage the appropriate Adobe Flash exploit to take over the user’s machine. From there, the RCS agent was inside and able to move to the next stage of the malicious operation.
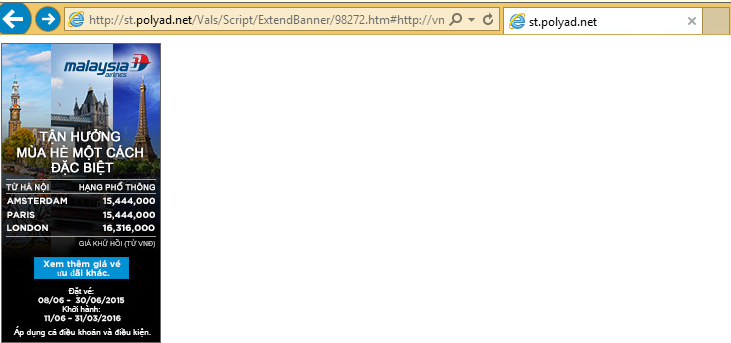 An example of a Vietnamese-targeted campaign redirecting a non-targeted individual using IE to an advertisement.
An example of a Vietnamese-targeted campaign redirecting a non-targeted individual using IE to an advertisement.
We were able to track this process by reverse engineering the files on the delivery server and JSON logs of “customer” communication. Digging deeper into the data, we were able to see when Hacking Team infiltrated a target (down to the last second), where they were located, what ISP they used, what operating system, and even which build of their browser was used to access the delivery server. For one target based in Egypt, we were able to see that they were using Chrome build 43.0.2357.130, which was released on June 22. Hacking Team infiltrated their system using the Flash exploit just six days later on June 28. This is both important, and amusing, considering Chrome is marketed as the most secure browser for the average user, but they were able to exploit it in a matter of days after the most recent update at the time.
What is also interesting about the attack is what we were able to glean about the delivery server itself, which was hosted at mynewsfeeds.info. (You may want to check your firewall and corporate proxies for this URL, in case your organization was targeted by Hacking Team!) We tracked the URL and WhoIs information to see where the team had registered it to. In fact, the registration information for their domain pointed to a rundown apartment complex in a bad neighborhood in Tel Aviv! However, the location and name associated with the WhoIs - David Cohen, the Israeli equivalent of “John Smith” - were an obvious misdirection. Not only did the team clone the techniques of Flame, which is attributed to Israel, but they also falsified their domain registration as if it were based in Israel.
One file we found related to the mynewsfeeds.info domain on VirusTotal.com was tmp_privesc, a binary which contains a privilege escalation exploit using an Adobe driver that is present on both Windows and Mac OSX operating systems. This could be the “smoking gun,” which allowed the usage of this exploit in the wild, and would allow us to identify it much more quickly on endpoints, which we will touch on more in a future write up. By leveraging Virus Total as one of our threat intelligence sources, we can apply machine learning and big data to cross examine the information from the data dump and better identify these tactics and tools when they are used again in the future.
We also found it important to note that the mynewsfeeds.info domain only had a few hashes associated with it before the Hacking Team leak. However, since then more than a dozen have cropped up, and while these weren’t found to be harmful, they all include the hash of the newsfeeds domain embedded in them - likely a result of numerous groups now downloading, compiling and running the code themselves.
This is only part of our analysis of the data downloaded from Hacking Team, and as we move forward in our research we will continue to provide updates that the security community may find valuable. We hope this analysis and description of Hacker Team’s tactics proves useful for other InfoSec professionals. Stay tuned for further analysis and other updates from our team.
You can follow Amit and Alex on Twitter at @0xAmit and @awfrazer.

Lital is a Marketing Team Leader, Storyteller, Technology Marketing Expert. She joined Cybereason as the first marketing hire and built a full marketing department. Specializing in brand building, product marketing, communication and content. Passionate about building ROI-driven marketing teams.

Pete Herzog, co-founder of ISECOM and Hacker Highschool, wants our kids to learn about cybersecurity - especially the more advanced stuff like security analysis and hacking - check it out...

Due to some controversy in the community over the airplane hacking episode, we have decided to remove it from the playlist...

Pete Herzog, co-founder of ISECOM and Hacker Highschool, wants our kids to learn about cybersecurity - especially the more advanced stuff like security analysis and hacking - check it out...

Due to some controversy in the community over the airplane hacking episode, we have decided to remove it from the playlist...
Get the latest research, expert insights, and security industry news.
Subscribe