So, what does 2018 hold in store for the defenders? Cybereason researchers and analysts identified the following as some of the bigger security trends for the new year:
01. SUPPLY CHAIN ATTACKS INCREASE & REMAIN UNDERREPORTED
02. DESTRUCTIVE ATTACKS DO NOT LET UP
03. THE LINE BLURS BETWEEN APT ACTORS & CYBERCRIMINALS
04. FILELESS MALWARE ATTACKS BECOME UBIQUITOUS
Defenders will always face challenges as they attempt to protect their organizations, and no one likes end-of-the-year security reports that are all doom and gloom. And the more our researchers and analysts talked about what to expect in 2018, the more there was a cause to believe that the situation could actually improve for the good guys and gals next year. There was a bit of optimism peppered among their talk of ransomware, wipers, malwareless attacks and other security nasties. Organizations, they said, are finally understanding that cybersecurity really matters and encompasses more than buying antivirus software or setting up firewalls. The entire company needs to toe the line and adopt a security mindset. And this leads to the final prediction:
05. 2018: THE YEAR OF THE DEFENDER
Download the report
But first, a look back on 2017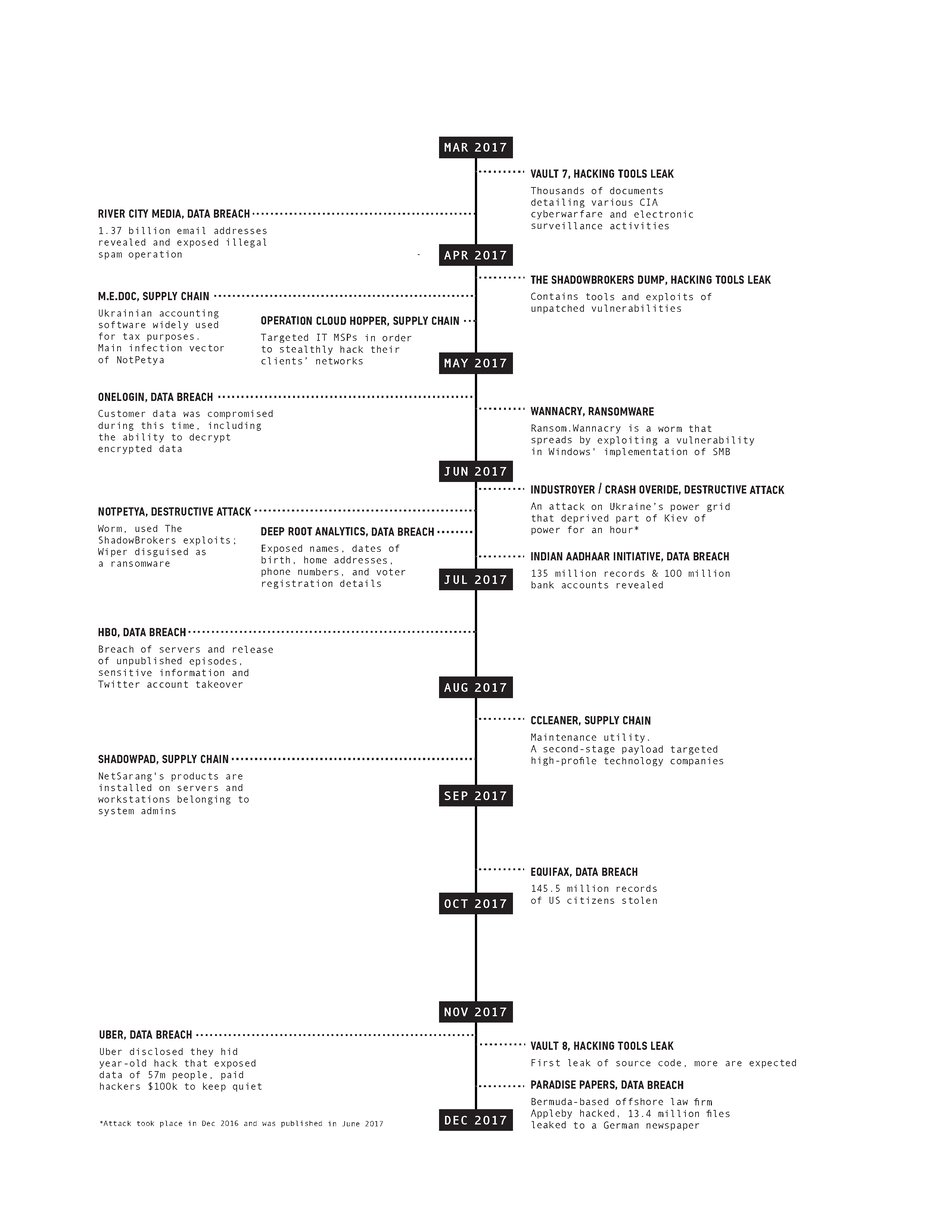
Cybersecurity Predictions for 2018
Chain, chain (supply) chain of attacks will increase next year, but will remain underreported. Supply chain attacks enable hacking at scale: the attackers build a hacking operation that targets one organization, and through it are able to gain an initial foothold and further compromise hundreds and sometimes thousands of organizations. When combined with other automated mechanisms, these operations can be scaled up, which allows many organizations to be compromised at the same time. This powerful shift helps drive the economics in favor of the attacker.
In 2018, destructive attacks (those that look to wipe out data on a computer instead of holding it for ransom) will get worse. The general trend, especially since 2010, has been an increase in attacks that were carried out using relatively simple, but capable, destructive malware.As more actors become emboldened by the lack of consequences for conducting cyberattacks, we are going to see an increase in destructive cyberattacks next year.
The commoditization of advanced toolsets and the public disclosure of attack techniques have caused the APT gang to fall from fine dining to fast food. The lines have blurred between the attack capabilities of nation-state players and those of the lower-level cybercriminals groups. Techniques and tools that were once used by a few APT actors have been adopted by dozens of other threat actors.
Fileless malware attacks are the new normal: While there’s been a lot of buzz around this tactic more recently, it’s actually been around for awhile. You’re hearing more about it now because in recent years this technique has found its way into the toolkits of more common cybercriminals as they rely less on traditional toolkits to carry out their attacks. Adversaries are also turning to fileless malware attacks since there are numerous readily-available style="background-color: transparent;">tools and ready-to-use scripts that make creating PowerShell payloads particularly easy.
We're deeming 2018 as the year defenders will truly be empowered. It is rather optimistic, but we have our reasoning: Organizations have made small, yet meaningful strides around reducing the number of days to identify and contain a breach. Thanks to the General Data Protection Regulation (GDPR), a new E.U. regulation that governs how businesses protect the data and privacy of E.U. citizens, companies around the world will have to get aboard the cybersecurity train. Destructive attacks like NotPetya made the importance of effective cybersecurity a board-level topic once and for all. And with boards paying more attention to cybersecurity in 2018, their support will further empower the defender. Lastly, fileless malware attacks have prompted a change in detection capabilities and solutions. The hype cycle has risen to a point where it is finally on every security team’s and organization’s agendas. And we'll see a shift next year in how security teams handle these types of threats.
In The Year of the Defender report, you can review the big cyberattacks of 2017, learn more about what lies ahead in 2018 and steps you can take now to mitigate these risks.
Want to listen instead? Watch our on-demand webinar. Hear Cybereason CSO Sam Curry and Senior Content Director Lital Asher-Dotan discuss our five 2018 security predictions.






