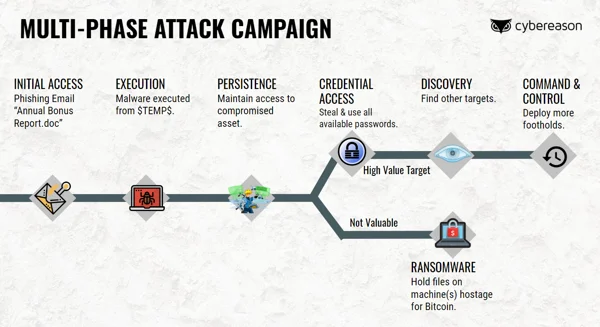
In this special attack simulation, get an inside look at how multi-stage attack campaigns operate today. You will witness the attacker’s infiltration and watch the malicious operation as it moves across the entire environment. See the many opportunities an attacker has to advance the operation, and the ways a defender can break the kill chain and end the attack before crown jewels are compromised.
Today’s attackers are able to translate a successful phish into persistent, stealthy network compromise. How does this happen, and what can we do to stop it?
In today's reality where prevention measures aren't always enough and penetration can seem inevitable, we -- the defenders -- need to out think, outpace, and quickly end even the most sophisticated attack.
You’ll come away with new knowledge on today’s attack campaigns and insights on how defenders can gain the upper hand. The session will share the attacker’s mindset and how it impacts our strategies as defenders.
Eric Sun is a Product Director at Cybereason, focused on helping security teams measure and improve their resilience against modern threats. Eric works closely with the Nocturnus research team and global SOCs to understand emerging attack campaigns and evolving best practices. He brings a layer of behavior analytics and risk management from his many years in Asia as a professional poker player.
ERIC SUN, PRODUCT DIRECTOR, CYBEREASON
