The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
What's Happening?
The GSOC Cybereason Managed Detection and Response (MDR) Team is investigating a series of recent infections that use the SolarMarker backdoor. SolarMarker enables attackers to execute commands, PowerShell scripts, and Windows executables on compromised systems, and to deploy additional malware. The malware author uses the .NET framework to implement SolarMarker.
Key Observations
-
- The SolarMarker backdoor enables attackers to execute arbitrary commands, PowerShell scripts, and Windows executable files on compromised systems.
- SolarMarker can deploy additional malware on compromised systems. For instance, SolarMarker often deploys the Jupyter infostealer.
- For deployment, SolarMarker employs a multi-stage PowerShell loader that uses a variety of obfuscation techniques, such as encryption, string encoding, and string concatenation.
SolarMarker Backdoor Analysis
A SolarMarker infection exhibits the following malicious activity:
-
- An executable file named, for example, ways-of-working-document-template.exe, executes on a victim system in the context of a user. The executable file then drops a file that has the .tmp extension, such as C:\Users\user\AppData\Local\Temp\is-BIKHB.tmp\ways-of-working-document-template.tmp, in the user’s temporary folder. The .tmp file then executes with a command-line parameter that has a specific format, such as /SL5="$5240E,131849241,999424,C:\Users\user\Downloads\ways-of-working-document-template.exe".
- The .tmp file drops a file in the user’s home directory, for example, C:\Users\user\501028bd84dbba5ff2685f83d3c7fc1b\30149c5df530081663233aec6930de0e\4fbea8ba0531eb01d2dfed68d4a48b2b\34eae20ce9de7a56447247343dee3e91\4e67b9428c6924a805e77a518fc278e1\534ef8283f8a022abfbf8f4cc69ab3c4\714d2c1a6197831981d2b8fa588cb6cf. This file is Base-64 encoded and encrypted with a hardcoded key. The .tmp file then executes a PowerShell script. The PowerShell script decodes and decrypts the contents of the dropped file, which results in PowerShell code. This decrypted PowerShell code then executes.
The .tmp file may also execute legitimate software, such as software installers, as part of a smokescreen technique for masking malicious activities:
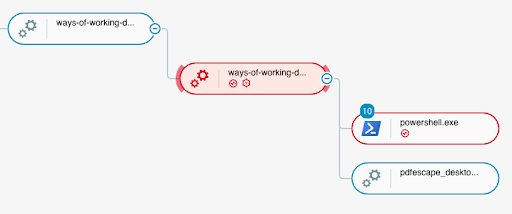 The .tmp file (ways-of-working-document-template.tmp) executes PowerShell code and a legitimate installer file (pdfescape_desktop_installer.exe)
The .tmp file (ways-of-working-document-template.tmp) executes PowerShell code and a legitimate installer file (pdfescape_desktop_installer.exe)
-
- The decrypted PowerShell code conducts the following activities:
- The code creates multiple files in the user’s AppData folder (for example, in the C:\Users\user\AppData\Roaming\Microsoft folder). These files have random names and contain random content, except for one file, which is a PowerShell script.
- For persistence, the code then uses the Register-ScheduledTask and Start-ScheduledTask commands to register and start a scheduled task that has a random name, such as cjvfFNQTVYEkaDrIMuexzowqRCsWglGByHAdiKmLSphUJZPXtnO. This scheduled task starts at system startup and executes the PowerShell script stored in the user’s AppData folder.
- Alternatively, for persistence, the PowerShell code creates a shortcut, a .lnk file that has a random name, in the user’s startup folder (for example, C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\a106545bbf446b8ad0db8c211c791.lnk). This shortcut executes the PowerShell script stored in the user’s AppData folder. The PowerShell code then reaches a code segment that is identical to the code of the PowerShell script that is stored in the user’s AppData folder and that executes at system startup. The code segment conducts the following activities:
- The PowerShell code decodes and decrypts an encrypted .NET assembly payload from a variable.
- The PowerShell code uses the [System.Reflection.Assembly]::Load function to reflectively load the .NET assembly, and then executes the [Mars.Deimos]::Interact function that the assembly implements:
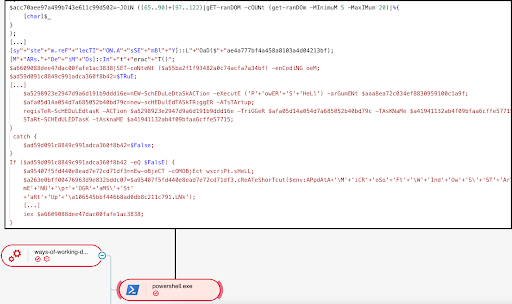 Execution of the decrypted PowerShell code
Execution of the decrypted PowerShell code
-
- The [Mars.Deimos]::Interact function first collects information about the compromised system, such as computer name, operating system version, platform architecture, and user permissions. The function then generates an ID that uniquely identifies the compromised system and stores this ID as a file named solarmarker.dat in the user’s AppData folder (for example, C:\Users\user\AppData\Roaming\solarmarker.dat). The [Mars.Deimos]::Interact function then follows an established communication protocol to exchange messages with an attacker-controlled endpoint. This endpoint issues one of two different commands to the compromised system:
- command: This command causes an attacker-provided PowerShell command to execute on the compromised system.
- file: This command causes an attacker-provided PowerShell script or a Windows executable file to execute on the compromised system.
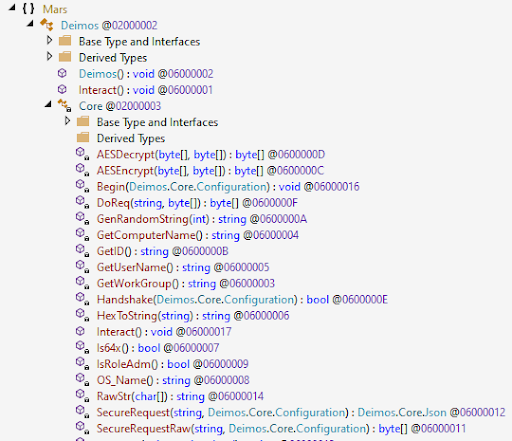 Functions implemented as part of the reflectively loaded .NET assembly, including [Mars.Deimos]::Interact
Functions implemented as part of the reflectively loaded .NET assembly, including [Mars.Deimos]::Interact
Cybereason Recommendations
Cybereason recommends the following:
-
- Set the features of the PowerShell and .NET protection of the Cybereason platform to Detect or Prevent. The Cybereason platform labels PowerShell processes involved in SolarMarker deployment as suspicious.
- Threat Hunting with Cybereason: The Cybereason MDR team provides its customers with custom hunting queries for detecting specific threats - to find out more about threat hunting and Managed Detection and Response with the Cybereason Defense Platform, contact a Cybereason Defender here.
- For Cybereason customers: More details available on the NEST including custom threat hunting queries for detecting this threat.
About the Researchers:
Aleksandar Milenkoski, Senior Threat and Malware Analyst, Cybereason Global SOC
 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Eli Salem, Senior Security Analyst, Cybereason Global SOC
 Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.







 Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system.
Aleksandar Milenkoski is a Senior Threat and Malware Analyst with the Cybereason Global SOC team. He is involved primarily in reverse engineering and threat research activities. Aleksandar has a PhD degree in the area of system security. Prior to Cybereason, his work was focusing on research in the area of intrusion detection and reverse engineering security mechanisms of the Windows 10 operating system. Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
Eli Salem is a lead threat hunter and malware reverse engineer at Cybereason. Eli has worked in the private sector of the cyber security industry for a couple of years now. In his free time he publishes articles about malware research and threat hunting.
