The MITRE Engenuity ATT&CK® Evaluations for Enterprise has quickly become the de facto authority for measuring the effectiveness of security solutions against real world scenarios that mimic advanced persistent threat attack progressions.
More details here: Cybereason Posts Best Results in History of MITRE ATT&CK Evaluations
With the release of the 2022 ATT&CK Evaluations results, many vendors are scrambling to cherry-pick the results and spin up some clever interpretations of the data that put the best light possible on their offerings. At Cybereason, we are proud to let the unadulterated evaluation results speak for themselves...
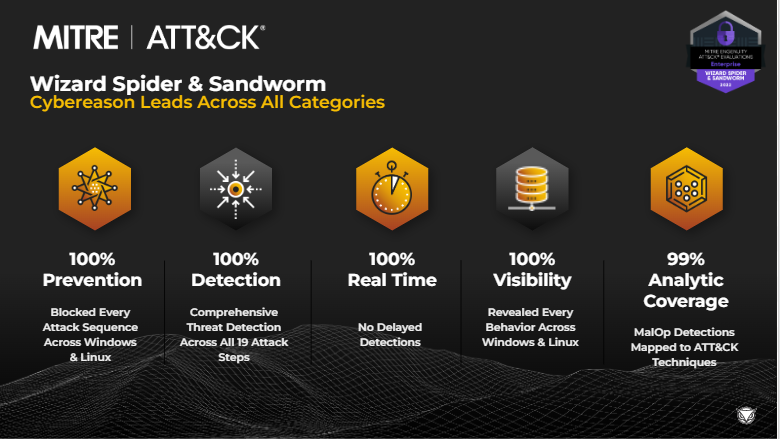
Cybereason achieved perfect scores in nearly every aspect of the MITRE ATT&CK Evaluations
- 100% Prevention: Cybereason detected and prevented 100% of the 9 different attack sequences evaluated for both Windows and Linux
- 100% Detection: Cybereason detected 100% of all 19 attack steps by Wizard Spider and Sandworm
- 100% Visibility: Cybereason exposed 100% of the 109 different attack behaviors evaluated for both Windows and Linux
- 100% Real-Time Protection: Cybereason had zero delayed detections
- 99% Analytic Coverage: Cybereason detections mapped back to the key ATT&CK techniques evaluated
- Minimal Configuration: Cybereason delivered out-of-the-box protection with minimal (<3%) configuration changes required
- More Details Here and a handy one-pager available here (PDF)
Round 4 of the ATT&CK Evaluations highlights the efficacy of our NGAV and EDR capabilities in protecting against sophisticated attack techniques from threat actors like Sandworm and Wizard Spider. In addition, the Cybereason XDR Platform delivers AI-driven prevention, detection and predictive response protection that identifies and blocks advanced threats at the earliest stages of an attack.
The results from all four years of the ATT&CK Evaluations highlight how the Cybereason solutions map directly to the ATT&CK framework to deliver unparalleled detection of advanced threat actor Tactics, Techniques, and Procedures (TTPs). The superior out-of-the-box efficacy that the AI-driven Cybereason XDR Platform delivers means there is little need for solution configuration changes at deployment.
Organizations can immediately benefit from exceptional real-time prevention and detection capabilities, automated and one-click predictive response options to stop the most advanced cyberattacks.
Join us for a live webinar on April 7th where we will boil down the complexity of the MITRE ATT&CK framework so your organization can better understand:
- How to interpret the results across Protection, Detection for Windows and Linux
- The difference between Technique, Tactic and Telemetry detections
- Why organizations are mapping to the MITRE ATT&CK framework and what’s next
- REGISTER HERE
MITRE Engenuity ATT&CK Evaluations and the Enterprise
Organizations are increasingly mapping their threat detection strategies to the ATT&CK framework, which provides a common language for Defenders to understand the range of techniques adversaries can use to gain initial access, escalate privileges, steal account credentials, move laterally in the targeted network, and ultimately to exfiltrate sensitive data or disrupt critical business operations.
The MITRE Engenuity ATT&CK Evaluations reveal how vendors approach the same challenges in reducing the time required to identify, understand and respond to malicious actions before material damage occurs. We believe the results highlight the effectiveness of Cybereason under real-world conditions because:
- The AI-driven Cybereason XDR Platform identifies attacks earlier by correlating behavioral telemetry across the entire network, including the broad range of device types, user identities, application suites, cloud workloads and more.
- The Cybereason MalOp™ reduces mean time to detection and response (MTTD and MTTR) by immediately providing the complete attack story from root cause without the need for complex queries.
- Cybereason delivers actionable detections and predictive response across all measured MITRE ATT&CK evaluation categories without inundating analysts with a barrage of uncorrelated alerts.
Cybereason and MITRE CTID: Attack Flow Project
Cybereason also collaborates with MITRE Center for Threat-Informed Defense (CTID) on the Attack Flow Project, which seeks to develop a common data format for describing sequences of adversary behavior in order to improve defensive capabilities.
The goal of the Attack Flow Project is to generate a machine-readable representation of a sequence of attacker actions and context along with specific descriptive attributes of those actions and assets composed of five main objects: the flow itself, a list of actions, a list of assets, a list of knowledge properties, and a list of causal relationships between the actions and assets.
Cybereason joined the Center as a Research Participant to conduct research and development to support further evolution of the MITRE Engenuity ATT&CK framework. Cybereason and the Center work to provide Defenders with a deep understanding of adversary tradecraft and advances in the development of countermeasures for prevention, detection and response to complex threats.
Cybereason is dedicated to teaming with Defenders to end attacks across the enterprise to anywhere the battle is taking place. Contact us today to learn how your organization can benefit from an operation-centric approach through the AI-driven Cybereason XDR Platform.






