The results of the latest ATT&CK Evaluation, conducted by MITRE Engenuity, are out! Our Cybereason Defense Platform was evaluated on its ability to prevent and detect advanced attacks, achieving 100% coverage for prevention of Windows and Linux-based threats, and 98% technique visibility across the 54 advanced attack techniques applied in testing. The MITRE Evaluation validates Cybereason’s future-ready attack protection, and superior prevention, detection and response capabilities (more details here).
This year’s evaluation emulated threat groups Carbanak and FIN7, who are known to attack banks, retail, and the hospitality sectors. As adversaries who attack financial organizations, it’s not surprising that the evaluation tested stealthy techniques including scripting, obfuscation, “living off the land” and -- new this year -- attacks against Linux systems.
In today’s threat landscape, it’s more important than ever that security investments prove their effectiveness in reducing the risk of cyberattacks. For this reason, the MITRE ATT&CK Framework along with the MITRE Engenuity ATT&CK Evaluations have been an invaluable resource for Defenders to speak a common language around threats, as well as a consistent way to measure cybersecurity vendor capabilities in detecting and stopping malicious operations.
Here’s a rundown of the exceptional performance of the Cybereason Defense Platform in this latest round of testing:
100% Protection Across the 10 Tested Malicious Operations
New to this year’s evaluation was prevention testing - the ability for a solution to block malicious activity. Across the 10 scenarios tested, Cybereason blocked all of the malicious operations, which included:
- Initial access with embedded VBE in Word Document
- Registry Shellcode and PowerView
- UAC Bypass and Mimikatz
- PS Exec with Pass-the-Hash
- Credential Access
- Initial Access and C2
- Privilege Escalation and Credential Access
- Expand Access
- BOOSTWRITE
- Shim Persistence
100% Detection of Malicious Operations on Linux Systems
Also new to this year’s evaluation was testing on Linux systems (CentOS 7.7). Cybereason had 100% coverage for the 12 ATT&CK techniques used on Linux systems, highlighting our strength in identifying post-compromise activity and parity between operating systems.
98% Coverage for the 54 ATT&CK Techniques Tested
In total, the 4-day evaluation tested 174 different variations of 54 ATT&CK techniques. Cybereason had excellent coverage across each tested kill chain. Notably, 99% of our Malops (malicious operations detections) were generated in real-time, and 97% were generated out-of-the-box, meaning that there were no configuration changes required to the product.
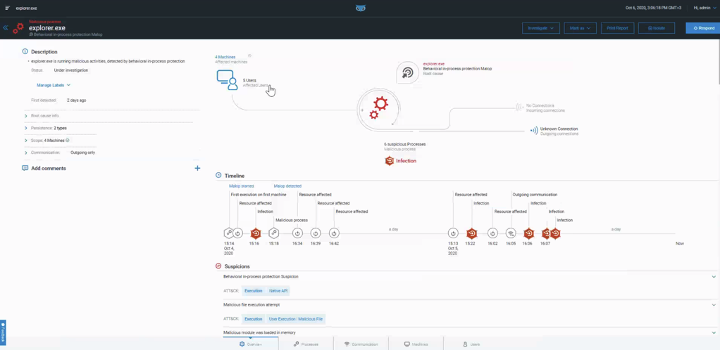
Cybereason took advantage of 12 different data sources in its analytics, producing highly correlated detections that map directly to MITRE ATT&CK. Cybereason doesn’t generate alerts, it exposes malicious operations: security analysts can quickly understand (1) root cause, (2) affected users and assets, (3) attacker tools and communications, (4) a timeline of events, and (5) suggested response actions.
To learn more about this year’s evaluation and how security teams are operationalizing ATT&CK, join us for a webinar, R3 MITRE ATT&CK ENGENUITY EVALUATIONS EXPLAINED, where Cybereason CISO, Israel Barak, will share our evaluation experience along with MITRE ATT&CK best practices.
Cybereason is dedicated to teaming with defenders to end cyber attacks from endpoints to the enterprise to everywhere. Talk to a Cybereason defender today or schedule a demo to learn how your organization can benefit from an operation-centric approach to security.