In the past two weeks, the Cybereason Intelligence Group has looked at the NotPetya attack. In this blog post, we'll share our latest thinking about the two actors vs one actor hypothesis behind this attack. Hopefully, by presenting our thoughts to the information security community we can work together to better understand the attack and figure out how organizations can better protect themselves from future campaigns.
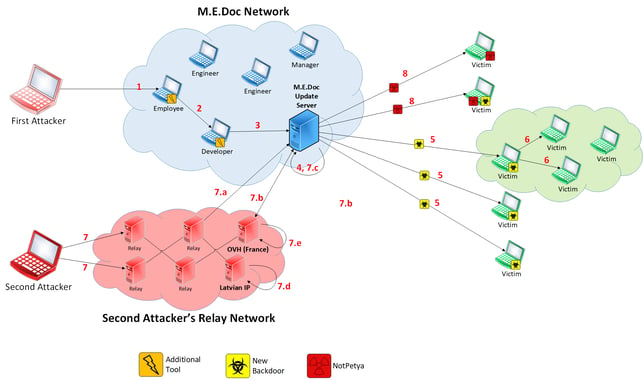
We theorize that an elaborate, well-planned campaign was conducted against M.E.Doc. The operation and attack progressed in two different ways, depending on whether there was a single actor or two. In this blog post we’ll explain our logic behind each theory.
Single actor
- In the beginning of 2017 attackers gained an initial foothold in M.E.Doc’s network, perhaps by a phishing email.
- Attackers leveraged the foothold to spread to developers and development infrastructure in the network.
- Attackers researched the accounting software, learned how it is built and operates, and accessed the update server and tainted the software update in April.
- The attackers access to updates was inconsistent, resulting in only some updates being weaponized. This may have caused the attackers to change tactics or the method of weaponizing.
- Attackers “sprayed” their backdoor to every client that installed the malicious update.
- The backdoors enabled the attackers to carry out advanced operations, including selecting victims based on unique Ukraine corporate tax identification numbers that were extracted from the software, conducting network reconnaissance, sending online commands and perhaps even permitting lateral movement in the network. Of course, most notably the attackers deployed NotPetya.
- On June 18 NotPetya was finally compiled to appear as a ransomware. This supposed disguise could be the result of:
- A mistake, bad planning or a cut and paste mishap involving the code of Petya.
- An attempt to buy time. The attacker needed some leeway to ensure that the wiper was working properly (one of the main NotPetya’s DLL requires an argument to determine how long to wait for the scheduled shutdown). The ransomware facade distracted victims and security researchers for a few hours to allow successful execution and propagation in most targets.
- Opportunism. If the attackers can milk a few bucks from victims regardless of the operational objectives, why not? And indeed, a few dozen victims paid the ransom, with the total sum paid nearing $10,000.
- Attackers employed NotPetya as a diversion act or as a tool to erase traces of their activity. Alternatively, the wiping was the attack’s real objective since it crippled the Ukraine. It was clear in advance that NotPetya will expose the backdoor and will burn M.E.Doc updates as an intrusion vector. By using a wiper, the attackers ad-hoc disabled retrieval of the “patient zero” in each victim company.
Two actors
- In the beginning of 2017, attackers gained an initial foothold in M.E.Doc’s network, perhaps by a phishing email.
- Attackers leveraged the foothold to spread to developers and development infrastructure in the network.
- Attackers researched the accounting software, learned how it is built and operates, and accessed the update server and tainted the software update in April.
- The attackers access to updates was inconsistent, resulting in only some updates being weaponized. This may have caused the attackers to change tactics or the method of weaponizing.
- Attackers “sprayed” their backdoor to every client that installed the malicious update.
- Until June 27 the attackers managed a covert campaign against M.E.Doc and its clients. Targets for further exploitation were hand picked based on the victim’s unique tax identification number and managed separately.
- On June 27, prior to the NotPetya outbreak, there were two external connections to the update serve: one from a Romanian IP owned by a French Web hosting company called OVH and another from a “dirty” Latvian server, both unrelated to M.E.Doc. These connections indicate a takeover or an override attempt by a second actor that discovered the operation and wanted to leverage or piggyback on it:
-
- 27/06/17 09:00 UTC - Second actor used stolen credentials of a M.E.Doc administrator to get root privileges on the update server
- 27/06/17 09:05 UTC - Second actor modified the configuration file for the NGINX server so that any traffic to update domain would be proxied through the OVH server.
- 27/06/17 12:33 UTC - The original server configuration is restored by first actor or by M.E.Doc admin.
- 27/06/17 14:11 UTC - SSH disconnect from a "dirty" Latvian IP (start time is unknown).
- 27/06/17 19:46 UTC - The OVH server was wiped.
- Second actor released NotPetya (that may have been designed for a different, yet similar need) to remove evidence of the operation it conducted, sabotage the campaign of the first actor or simply create chaos.
Conclusion
Like any other hypothesis around the NotPetya attack, the theories we presented have holes, inconsistencies and contradictions. Political motivations can make attribution murky while malware authors commonly use false flags to throw off security researchers. This mean that the information security community is still has much work to accomplish before fully understanding and contextualizing the entire chain of events surrounding NotPetya.






