The United Kingdom’s National Health Service (NHS) warned that scammers are in the process of sending out fake COVID-19 vaccine invitations. On January 25th, Urology Cancer Research & Education (UCARE) Oxford reached out to the NHS on Twitter and shared an image of one such fake invitation that it had received.
The Makeup of a Recent COVID-19 Scam Invitation
The scam email arrived with the subject line “NHSVaccination,” and it used stolen branding in an attempt to trick the recipients into thinking that the email was legitimate. In its body, the attack message informed the recipient that the NHS was in the process of “performing selections for coronavirus vaccination on the basis of family genetics and medical history.”
It then informed the recipient that they had been selected to receive the vaccine, at which point it instructed them to either accept or decline their invitation to receive the vaccine by clicking on one of two corresponding embedded links:

A screenshot of the scam email (Source: Twitter)
Someone at UCARE clicked on the “Accept invitation” link and found that it redirected to a website designed to impersonate the NHS. According to UCARE, that website subsequently asked for personal and financial information for the purpose of reserving its vaccine.
Cyber-security consultant Daniel Card examined the traffic data for the scam and found evidence that thousands of people had clicked the link leading to the fake NHS website. That being said, it was unclear how many people had submitted their information to it, Card told BBC News.
The NHS subsequently took to Twitter to remind users that the vaccine will always be free of charge and that the health service will never ask people to share their bank details in order to confirm their identity.
Not the First COVID-19 Vaccine Scam
The scam described above wasn’t the only instance in which digital fraudsters have attempted to prey upon interest surrounding COVID-19 vaccines. In the beginning of January, for instance, the Derbyshire Constabulary told BBC News it had received reports of a smishing campaign that informed recipients they were eligible to receive a vaccine.
Those messages instructed users to click on a link that, in turn, directed them to a fake NHS website designed to steal visitors’ financial information:
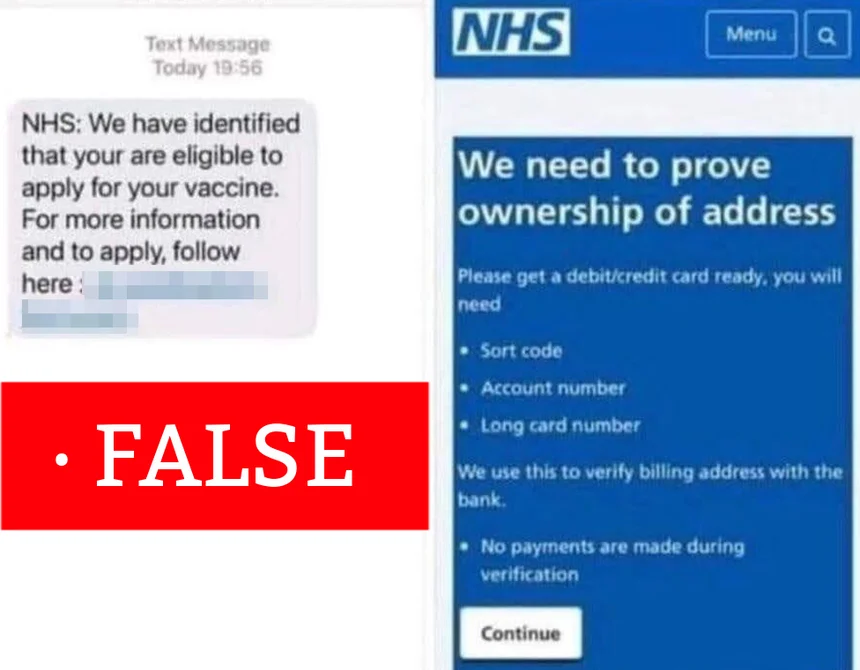
Screenshots of the fake text message and NHS site (Source: BBC News)
In service of public awareness, the NHS revealed on its website that all UK citizens are eligible to receive a vaccine and that they’ll be contacted by letter, text or email when it’s their turn to receive the vaccine. Additionally, it clarified that the vaccine is free of charge and that it’ll never ask people to supply their banking information, passwords and/or sensitive documents to confirm their identities.
COVID-19 vaccine ruses haven’t just appeared in the United Kingdom, either. On December 18, 2020, for example, the U.S. Attorney’s Office for the District of Maryland announced it had seized two fraudulent domains masquerading as the legitimate websites of pharmaceutical companies working on producing a COVID-19 vaccine.
Whoever registered those websites had apparently done so for the purpose of stealing visitors’ personal information, an investigation by the Department of Justice uncovered. It was around that same time when the FBI warned users to be on the lookout for schemes using COVID-19 vaccines as a lure for stealing victims’ personal information and money.
How to Defend Against Fake COVID-19 Vaccine Scams
Sam Curry, CSO for Cybereason, wasn’t surprised to learn of the campaigns discussed above:
“Do nation-state threat actors have no shame? Their year-long attacks on companies at the forefront of medical care and research has shown a cold-calculus,” Curry noted.
“Brazen attempts from state sponsored threat actors in China, North Korea, Iran and Russia to disrupt the COVID-19 supply chain, the administration of vaccines and the return to health of thousands of people that are sick with the virus are akin to acts of war, and one can hope these cyber thugs are eventually brought to justice.”
In the meantime, Curry recognizes that digital criminals will continue to target those who are looking to obtain a vaccination and try to steal their information. He therefore feels that it’s important for consumers to follow best practices when it comes to their email security.
“Consumers should never open attachments from untrusted people and sources, visit dubious websites or download information from untrusted places,” Curry said.
“To eliminate the cyber risk involved with scheduling a vaccination, go directly to the hospital's or clinic's website or make a phone call to do your scheduling. Never open an attachment via email, as phishing scams will continue so long as the market exists.”
Organizations can also take steps to protect themselves and their employees against these types of campaigns. They should specifically look to a platform that takes an operation-centric approach to security by detecting attacks at the earliest stages based on chains of malicious behaviors across the enterprise and not getting bogged down looking for IOCs after the attack has been successful. Learn more about why Cybereason excels in this regard.







