Highlights of the Attack
-
The Astaroth Trojan spam campaign is a Trojan most recently used to steal passwords and personal information from individuals in Brazil.
-
Brazil is a major contributor to global cybercrime that continues to have a plethora of new, nefarious activities targeting individuals.
-
The Astaroth Trojan disguises its payload as JPEG, GIF, and extensionless files to avoid detection.
-
The campaign exploits legitimate operating system processes as well as security vendor products from companies like Avast and GAS Tecnologia to gain information about the target machine and steal password information, as well as keystate information and clipboard usage.
- Full research on the latest Astaroth Trojan variant can be found here.
The Newest Astaroth Trojan
In this malware research, we explain one of the most recent and unique campaigns involving the Astaroth trojan. This Trojan and information stealer affected Europe and especially Brazil through the abuse of native OS processes and the exploitation of security-related products (in a similar fashion to how it’s abusing native OS processes).
Cybereason’s Active Hunting team was able to detect this new variant of the Astaroth
Trojan in a massive spam campaign that targeted Brazil and parts of Europe. The campaign maliciously took advantage of legitimate tools like the BITSAdmin utility and the WMIC utility to interact with a C2 server and download a payload. Uniquely, it was also able to use antivirus software Avast to gain information about the target system.
Brazil is constantly being hit with cybercrime. To read about another pervasive attack in Brazil, check out our blog post.

The spam campaign gained momentum towards the end of 2018 and was identified in thousands of incidents. In a short period of time, the attackers made dramatic changes to the process that improved its attack significantly. In the version of the malware we obtained, we noticed four unique, key differentiators from previous versions.
-
This version maliciously used BITSAdmin to download the attackers payload. This differed from early versions of the campaign that used certutil.
-
This version injects a malicious module into one of Avast's processes, whereas early versions of the campaign detected Avast and quit. As Avast is the most common antivirus software in the world, this is an effective evasive strategy.
-
This version of the campaign made malicious use of unins000.exe, a process that belongs to a Brazilian information security company GAS Tecnologia, to gather personal information undetected. This process is prevalent on Brazilian machines. To the best of our knowledge, no other versions of the malware used this process.
-
This version used a fromCharCode() deobfuscation method to avoid explicitly writing execution commands and help hide the code it is initiating. Earlier versions did not use this method.

Explaining the Attack
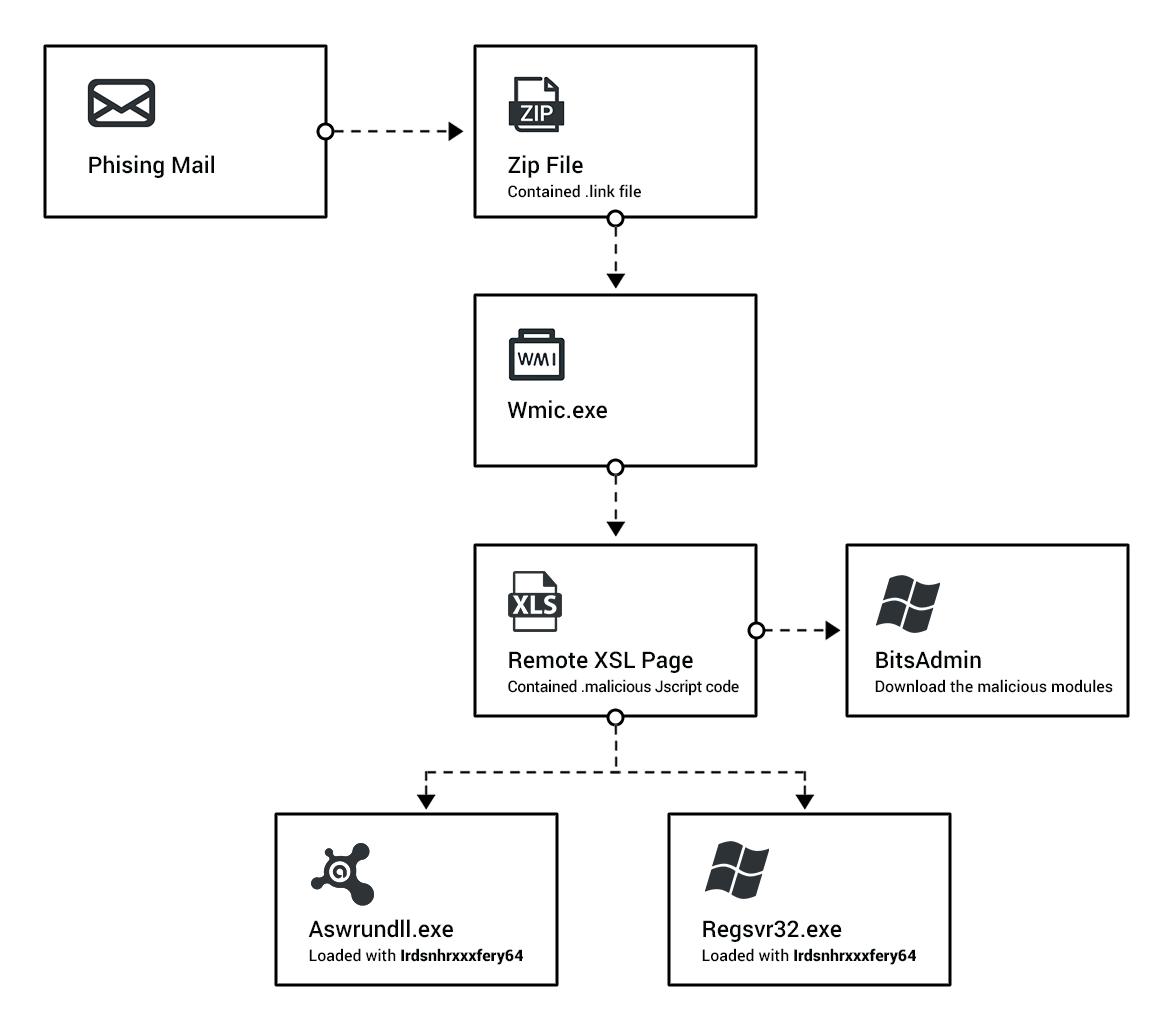
As with many traditional campaigns, this campaign begins with a .7zip file that gets downloaded to the user machine through a mail attachment or a mistakenly-pressed hyperlink. The downloaded .7zip file contains a .lnk file that, once pressed, initializes the malware. Upon initialization, a process spawns that uses the legitimate wmic.exe to initialize an XSL Script Processing attack. This attack allowed the malware to communicate with a remote C2 server and sent information like location information about the infected machine to the remote server.
The remote XSL script contains highly obfuscated code that is able to execute additional malicious activity. It uses several functions to hide its activities from antivirus defenses and researchers. This script is ultimately responsible for the malicious use of BITSAdmin to download the attackers payload to the target from a separate C2 server. The payload files are masqueraded as JPEGs, GIFs, and extensionless files, and contain the Astaroth Trojan modules.
Once the payload is received, it identifies if Avast exists on the infected machine. If so, it uses Avast to load a malicious module responsible for loading other modules and gathering information about the machine. A second module is loaded to collect and exfiltrate information like clipboard data, password information, and more.
Note:
aswrundll.exe is the Avast Software Runtime Dynamic Link Library that is responsible for running modules for Avast. aswrundll.exe is very similar to Microsoft’s own rundll32.exe - it allows one to execute DLLs by calling their exported functions. The use of aswrundll.exe as a LOLbin has been mentioned in the past year.
Impact of the Astaroth Trojan
Once the campaign has successfully infiltrated, it will log the users keystrokes, intercept their operating system calls, and gather any information saved to the clipboard continuously. With these methods, it uncovers significant amounts of personal information from the user bank accounts and business accounts. Additionally, in conjunction with NetPass, it gathers user login passwords across the board undetected, including any of their remote computers on LAN, mail account passwords, Messenger accounts, Internet Explorer passwords, and others.
Gathering this type of data can have a major impact on an organization and an individual. Getting access to account passwords can lead an attacker to potentially sensitive email correspondence, customer information, research and development information, and more. As with the 2016 DNC email leak, this can have considerable consequences. It can negatively impact the user, through loss of data from emails and loss of funds with stolen bank information. It can also affect the company, as their trade secrets and future research have been made public. This can result in loss of consumer trust, brand degradation, and competitor advantage.
The Astaroth Spam Campaign
The Cybereason Active Hunting Service was able to detect and evaluate an evasive infection technique used to spread a variant of the Astaroth Trojan as part of a large, Brazilian-based spam campaign. In our discovery, we highlighted the use of legitimate, built-in Windows OS processes to perform malicious activities and deliver a payload without being detected, as well as how Astaroth operates and installs multiple pieces. We also showed its use of well-known tools and even antivirus software to expand its capabilities. The analysis of the tools and techniques used in the Astaroth campaign show how truly effective these methods are at evading antivirus products. As we enter 2019, we anticipate that the using of WMIC and other living off the land binaries (LOLbins) will increase. Because of the great potential for malicious exploitation inherent in the use of LOLbins, it is very likely that many other information stealers will adopt this method to deliver their payload into targeted machines.
Continue to the full research on the latest variant of the Astaroth Trojan attack.
How does manual detection hinder security team productivity? Read about the seven struggles of detection and response in our eBook.