The ICS (industrial control system) environments that handle the generation, transmission and metering of energy have long been on the radar of attackers. In recent years attackers have hacked into the control system of a dam in New York, shut down the Ukraine’s power grid and installed malware on the OSes of U.S. companies in the energy, nuclear and water sectors. The U.S. government, realizing that a cyberattack on energy utilities would have major repercussions for businesses and citizens alike, this November will test the ability of the nation’s power grid to bounce back from a simultaneous cyberattack on electric, oil and natural gas infrastructure.
Watch our webinar on the latest dangerous attack on critical infrastructure.
The specter of cyberattacks against utility providers and the interest in protecting them come as the profile of adversaries who target ICS environments is broadening. While ICS attackers linked to APT (advanced persistent threat) groups and nation-state actors are still targeting these systems, a greater variety of threat actors with a range of skills is also going after ICS environments. That assessment is based on data collected from a honeypot Cybereason setup to emulate the power transmission substation of a major electricity provider.
Accompanying this variety of threat actors is a new approach to sourcing ICS assets. Instead of strategically selecting targets, performing through reconnaissance and targeting individuals with potential network access -- the typical infiltration path used by attackers who usually target ICS environments -- the actors who compromised Cybereason’s honeypot bought the asset off a dark Web forum. The playbook the attackers used after they compromised the network also differed from the traditional ICS threat actor profile and showed that while they had some advanced methods, a few of their techniques were sloppy.
Still, judging by how quickly these attackers operated, they’re very familiar with ICS environments, the security measures that utility providers implement and know how to move from an IT environment to an OT (operational technology) environment. Accessing the OT environment is the attackers’ ultimate goal since these systems operate the equipment that delivers power to homes and offices. Whoever controls the OT environment determines who gets utilities like electricity, natural gas and water.
Unlike other attackers who buy and sell access to compromised networks, the adversaries who purchased access to the honeypot showed no interest in partaking in more generic and less targeted activity like running botnets for cryptomining, spamming and launching DDoS attacks, said Cybereason CISO Israel Barak. In this case, the attackers had one intention: getting to the OT network.
“The attackers appear to have been specifically targeting the ICS environment from the moment they got into the environment. They demonstrated non-commodity skills, techniques and a pre-built playbook for pivoting from an IT environment towards an OT environment,” Barak said.
Despite displaying a level of sophistication, the attackers made some amateur moves that indicate their approach needs some refinement, said Ross Rustici, Cybereason’s Senior Director of Intelligence. He noted that the attackers disabled the security tools on one of the honeypot’s servers, a move that “made a lot of noise” and, in an enterprise, would draw the security team’s attention.
“The approach of going after ICS environments and ignoring everything else and living off the network to conduct activity is a level of sophistication you don’t normally see in honeypots. But they made some mistakes, raising red flags that don’t allow us to put them in that upper echelon of attackers. You don’t see that level of amateurism from APT actors who go after ICS environments,” he said.
For sale: Access to a power transmission substation’s IT and OT environments
The honeypot environment went live late in the second quarter and had a network architecture that’s representative of a typical power substation including an IT environment, an OT environment and HMI (human machine interface) management systems. The environment employed customary security controls including segmentation between the different environments.
The honeypot contained bait to entice attackers, including three Internet facing servers (Sharepoint, SQL and domain controller) with remote access services like RDP and SSH and weak passwords. Nothing was done to promote the servers to attackers. However, the servers’ DNS names were registered and the environment’s internal identifiers used a moniker that resembled the name of a major, well-known electricity provider.
Two days after the honeypot was launched, Cybereason determined that a black market seller had discovered it based on a toolset that had been installed in the environment. The tool -- xDedic RDP Patch -- is commonly found in assets that are being sold in the xDedic black market. It allows a victim and an attacker to use the same credentials to simultaneously log-in to a machine using RDP (Remote Desktop Protocol).
The seller also installed backdoors in the honeypot servers by creating additional users, another indicator that the asset was being prepared for sale on xDedic. The backdoors would allow the asset’s new owner to access the honeypot even if the administrator passwords were changed, a scenario that could have otherwise prevented the adversaries from accessing the servers.
Under new ownership
For the next few days, the honeypot was hit with cryptomining bots, phishing bots, DDoS bots, activity that Internet-connected assets typically experience. Then 10 days after the honeypot went live, the actor who is assumed to be the asset’s new owner connected to it using one of the backdoors created by the seller. The transaction most likely took place in a nonpublic channel, preventing Cybereason from obtaining information on how the payment was made.
Ain’t no security measure strong enough to keep me from you
After being stymied by the firewall, the adversaries began using a multipoint network reconnaissance process to identify potential paths from the IT environment into the OT environment. This approach assumes that different assets in an environment have different segmentation and network accessibility policies. For instance, in a typical IT/OT environment, certain assets (monitoring systems, data repositories and file servers, for example) that are hosted in the IT environment are also accessible from the OT environment. Using multipoint network reconnaissance the attackers move laterally to multiple assets and run parallel network discovery processes to locate an asset that is accessible to the OT network or any its HMI components.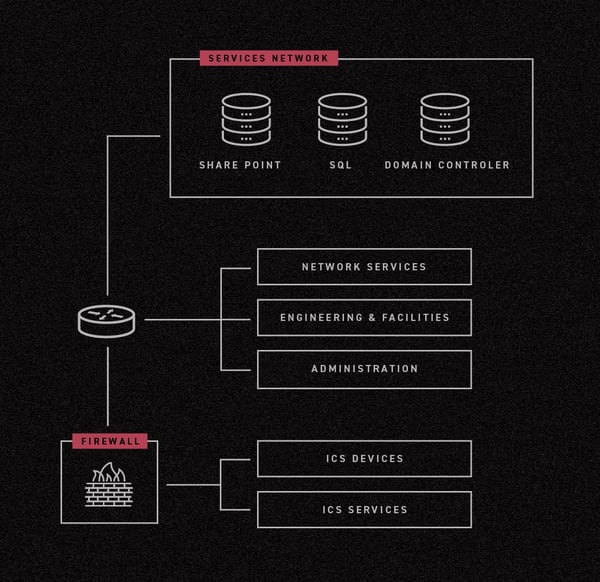
The attackers moved from the remote server to a Sharepoint server, to the domain controller to the SQL server, running network discovery to determine if one of these assets would allow them to access the ICS environment. Instead of scanning the full network, attackers focused on scanning for assets that would give them access to the HMI and OT controllers.
“In two days, the attackers got into the environment, conducted reconnaissance aimed at finding an entry point from the IT environment to the OT environment, which is really what they wanted,” Barak said.
What this means for security professionals
Barak suggested that organizations and companies with ICS environments operate a unified SOC that provides visibility into the IT and OT environments. As the honeypot demonstrated, attackers are looking to use IT environments as gateways into OT environments.
“Companies may have a NOC monitoring the OT environment, but a combined SOC lets you see all operations as they move through the network. Having this visibility is important because attackers could start in the IT environment and move to the OT environment,” Barak said.
Threat hunting is critical, he added. This activity looks for indicators that attackers are already in a company’s environment. Instead of waiting to react to an alert issued by a security tool, threat hunting allows defenders to take a proactive approach to security by detecting adversaries before they cause severe damage to a network.
The activity observed in the honeypot also suggests an increased risk for operators. The possibility that this is a trophy taker rather than an APT actor with training on these types of environments dramatically increases the risk of a mistake having real-world consequences.
“The biggest lesson learned from the honeypot is that multiple tiers of attackers find ICS environments interesting. That’s increasing risk for people who operate those types of systems. The security basics are really what’s going to prevent a bad day from becoming a catastrophic day,” Rustici said.
Many of these systems are old and fragile and even trained hacking units make mistakes that cause failures in these controls. Hackers seeking to make a name for themselves or simply prove that they can get into a system are far more likely to cause failures out of ignorance rather than malice. This makes incident response and attribution harder, but it also is more likely to result in an unintended real-world effect, he said.
Want more honeypot research? You’re in luck. A few months ago we setup another honeypot to emulate the environment of an investment company. This blog talks about what we found.






.jpg)
